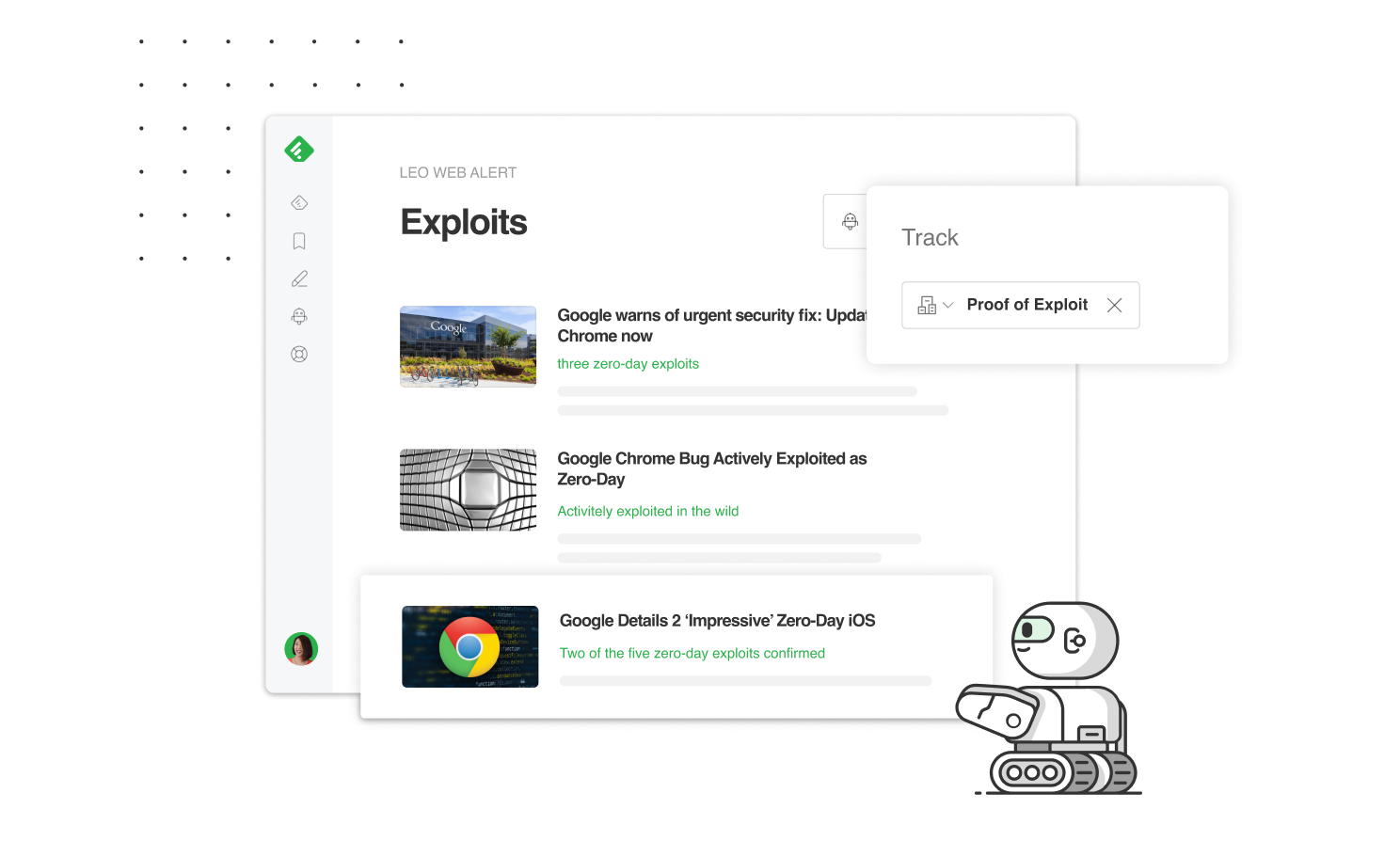
Does your team track emerging exploits across cybersecurity websites, code repositories, and social media sites?
We just released a new Proof of Exploit AI Model that I think you will find valuable.
This new machine learning model allows you to:
Curious how it works? Here is a tour
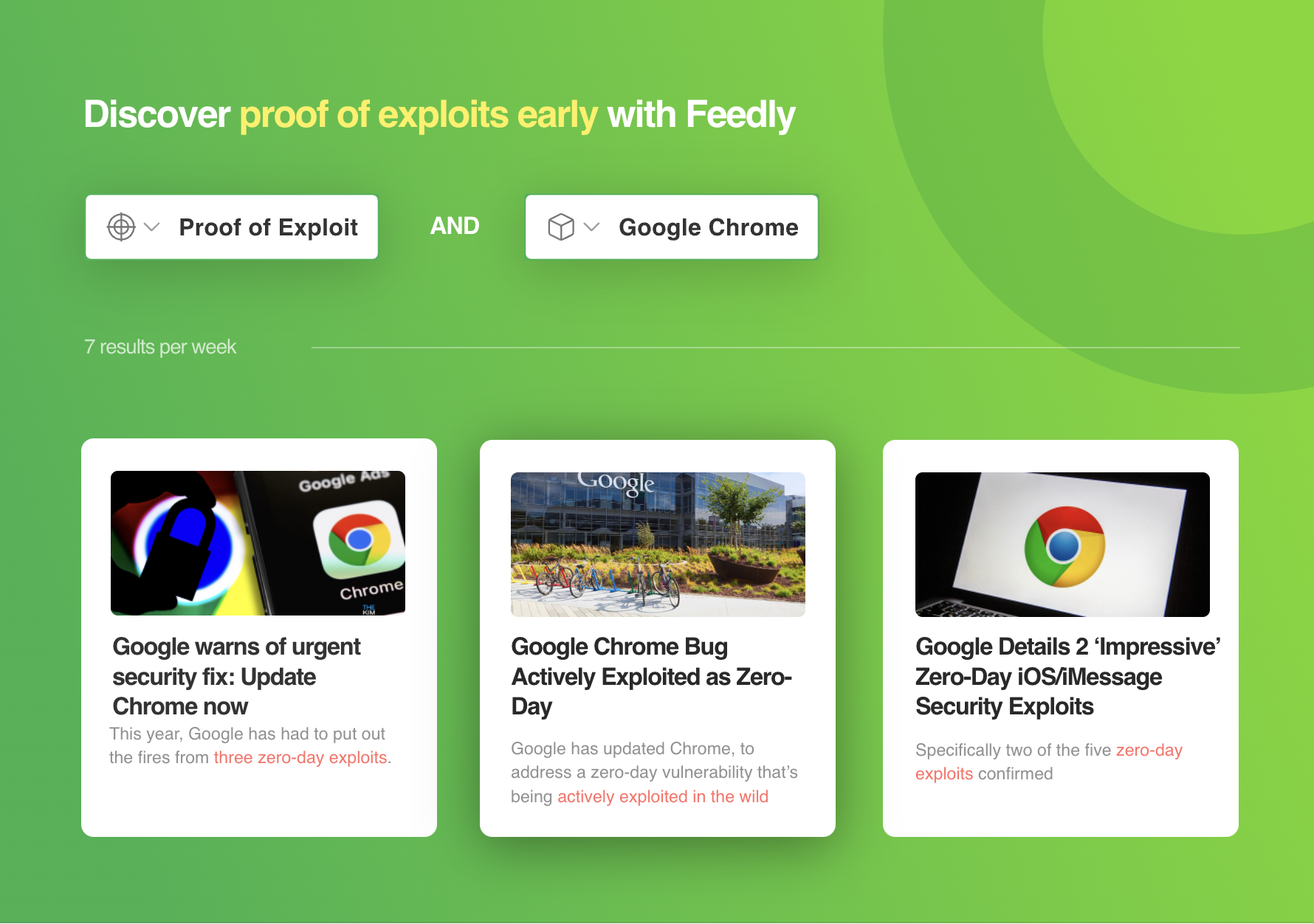
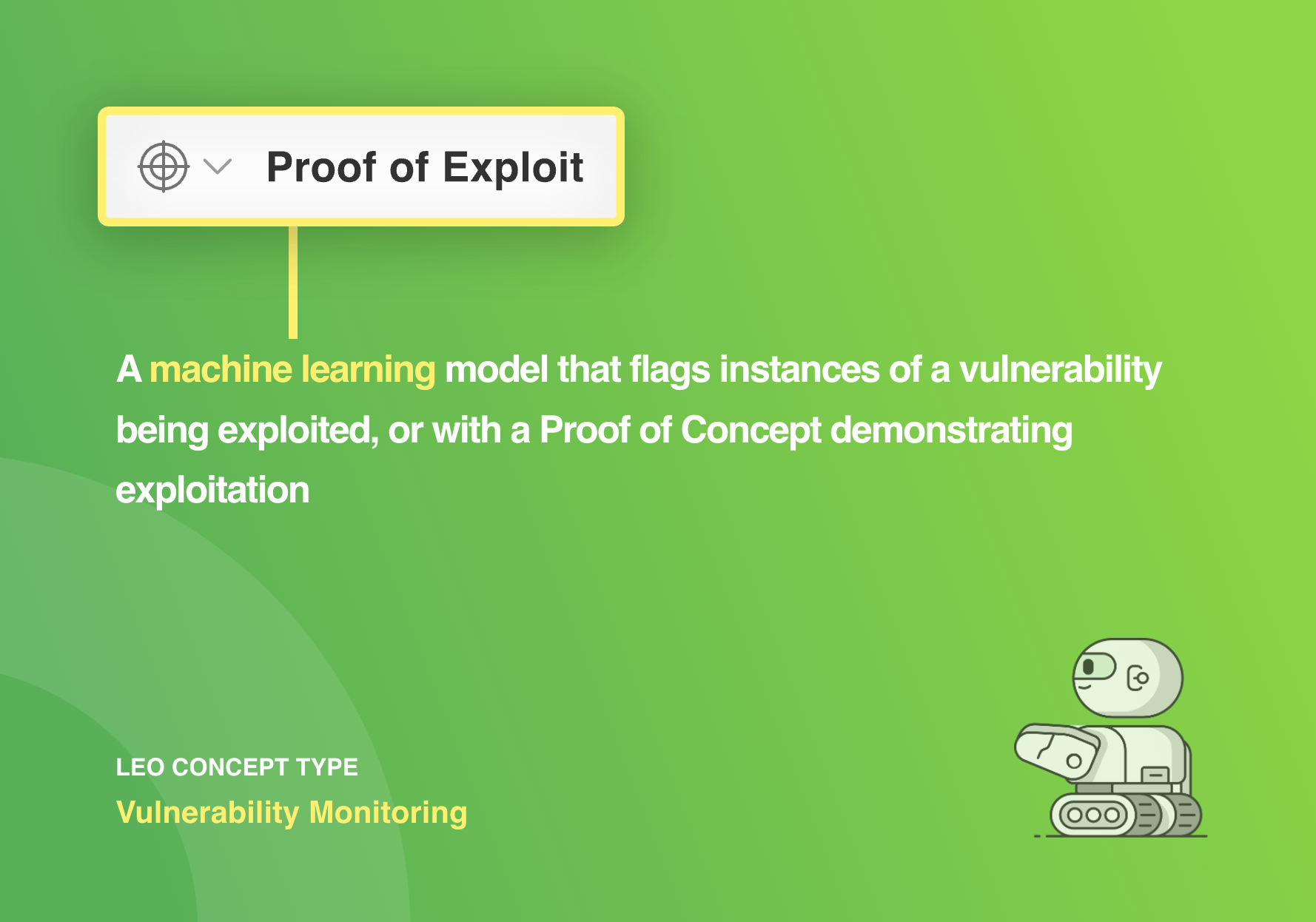


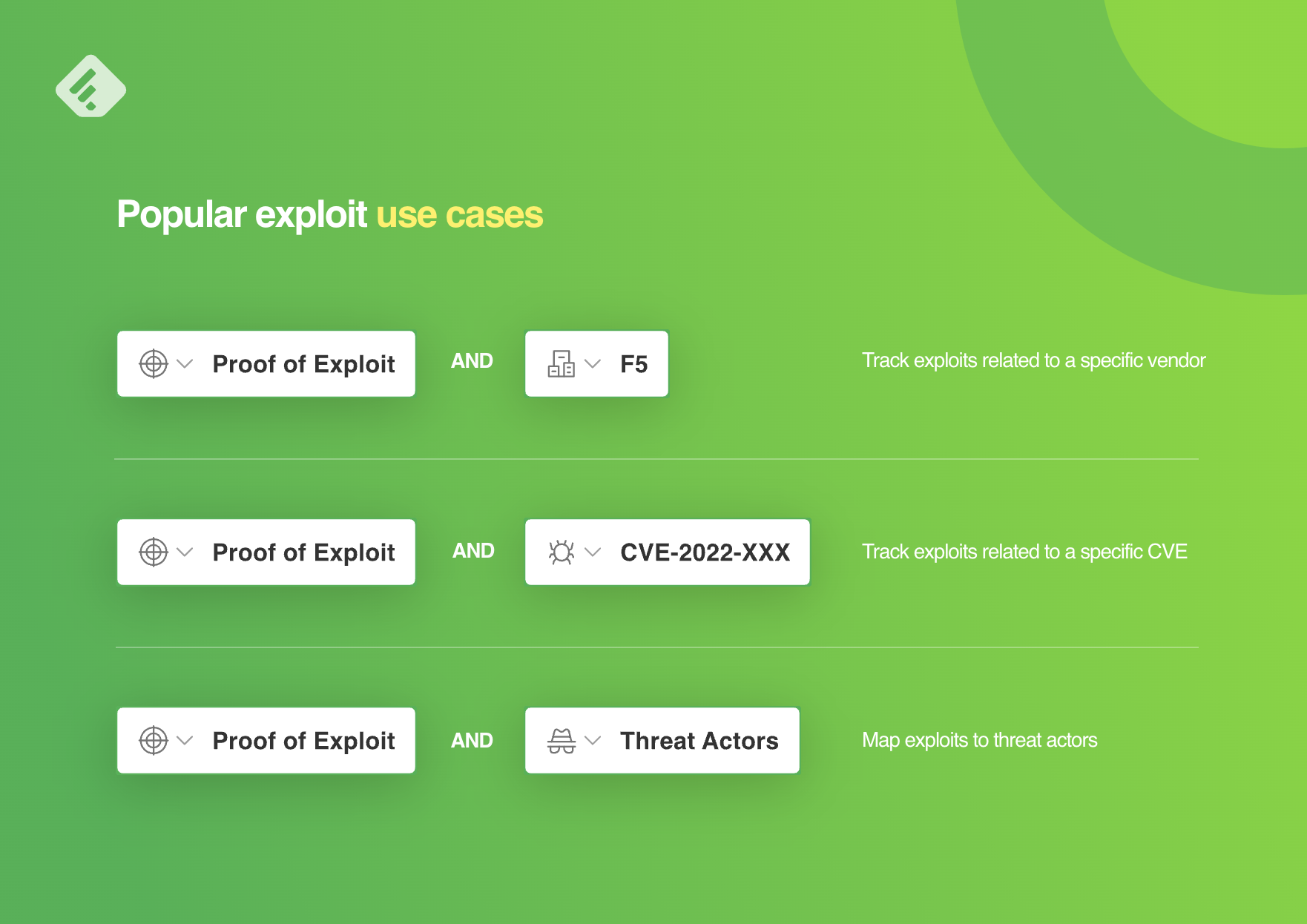
Proof of exploit is one of the machine learning models included in Feedly for Threat Intelligence. Start a free 30-day trial to see how Feedly can help you speed up your threat intelligence.

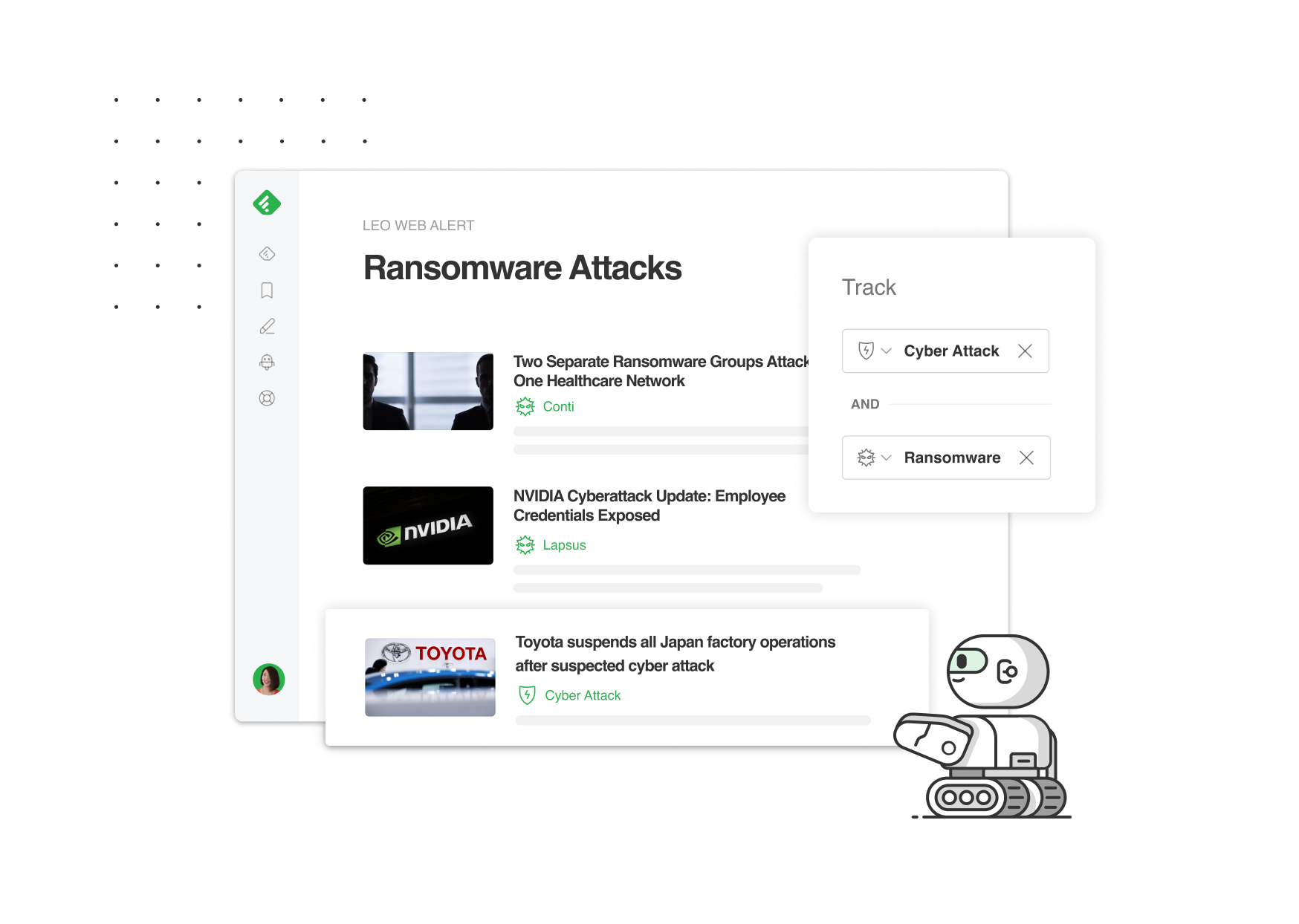
The core of Feedly for Threat Intelligence is an AI engine, that automatically gathers, analyzes, and prioritizes intelligence from millions of sources in real-time.
In this article, we’ll show you how to use AI Models to:
Before we look at those four use cases, let’s start with a short overview of how Feedly AI works.
Feedly AI reads millions of articles, reports, and social media posts every day and automatically tags key threat intelligence concepts: critical vulnerabilities, malware families, threat actors, indicators of compromise, ATT&CK techniques, companies, vendors, industries, etc.
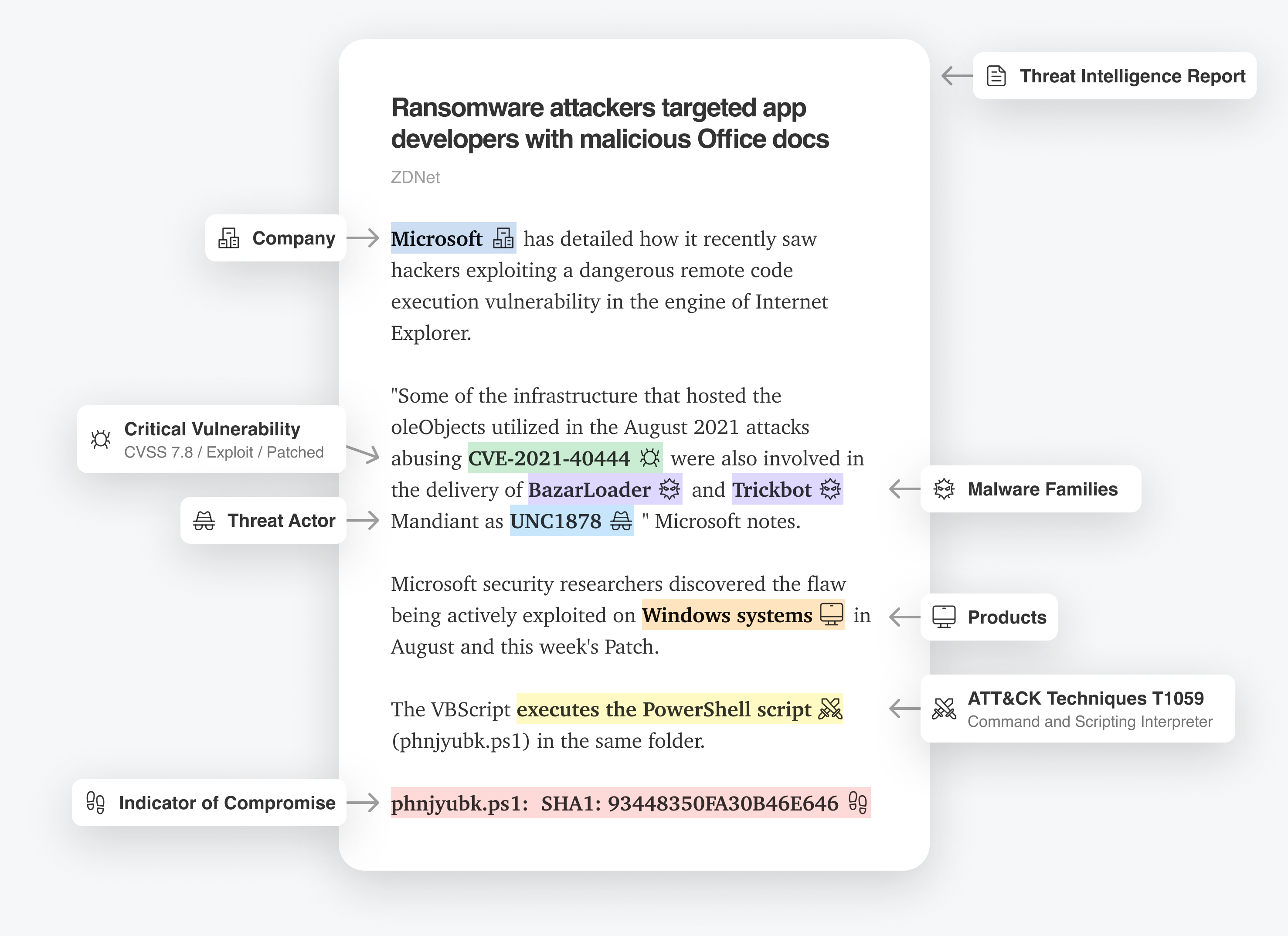
All this information is at your fingertips in near real-time via a powerful and intuitive search and tracking interface called (Feedly) AI Feeds.
Curious how it works? Let’s take a look at an AI Feed designed to track critical vulnerabilities and zero-days related to Cisco Systems:
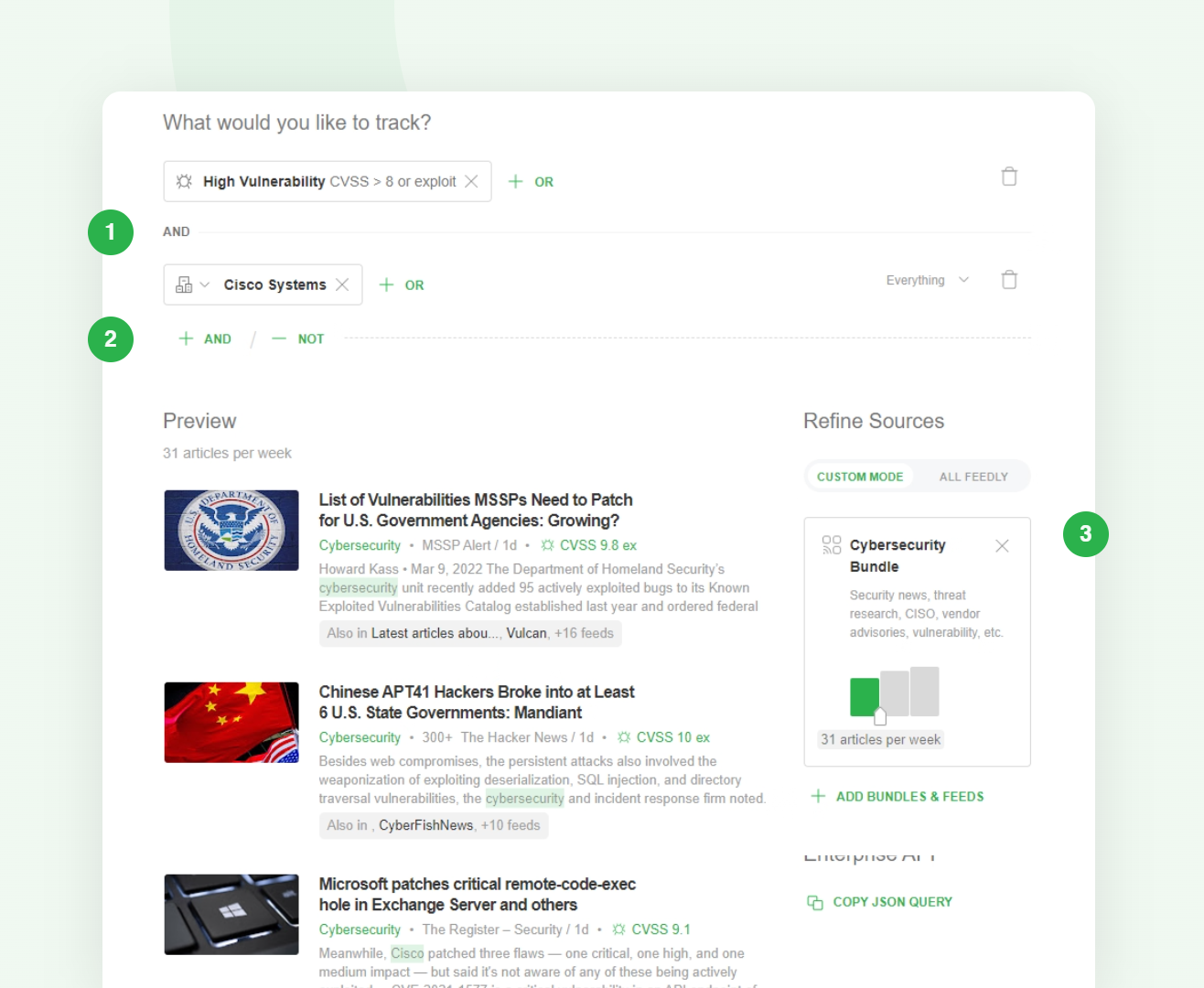
Creating an AI Feed is a three-step process:
With AI Feeds, you can add to a team or personal folder. New articles, reports, or social media posts matching the specified AI Models will appear in the AI Feeds.
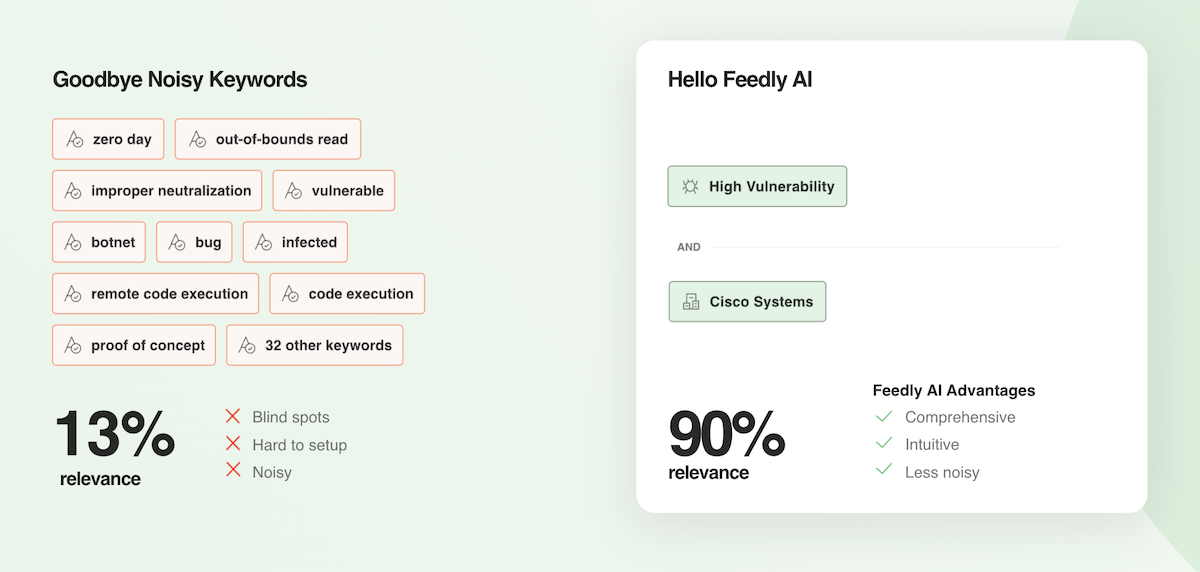
The power of AI Feeds is that ‘High Vulnerability’ and ‘Cisco Systems’ are not simple keyword matches. These AI Models are machine learning models that encapsulate a broader understanding of each concept:
Without AI Models, gathering intelligence would require a tedious effort of trying to find a long list of the right keywords, leaving room for blind spots and lots of irrelevant results.
Feedly for Threat Intelligence comes with a wide range of pre-trained AI Models so that you can easily translate your intelligence needs into AI Feeds.
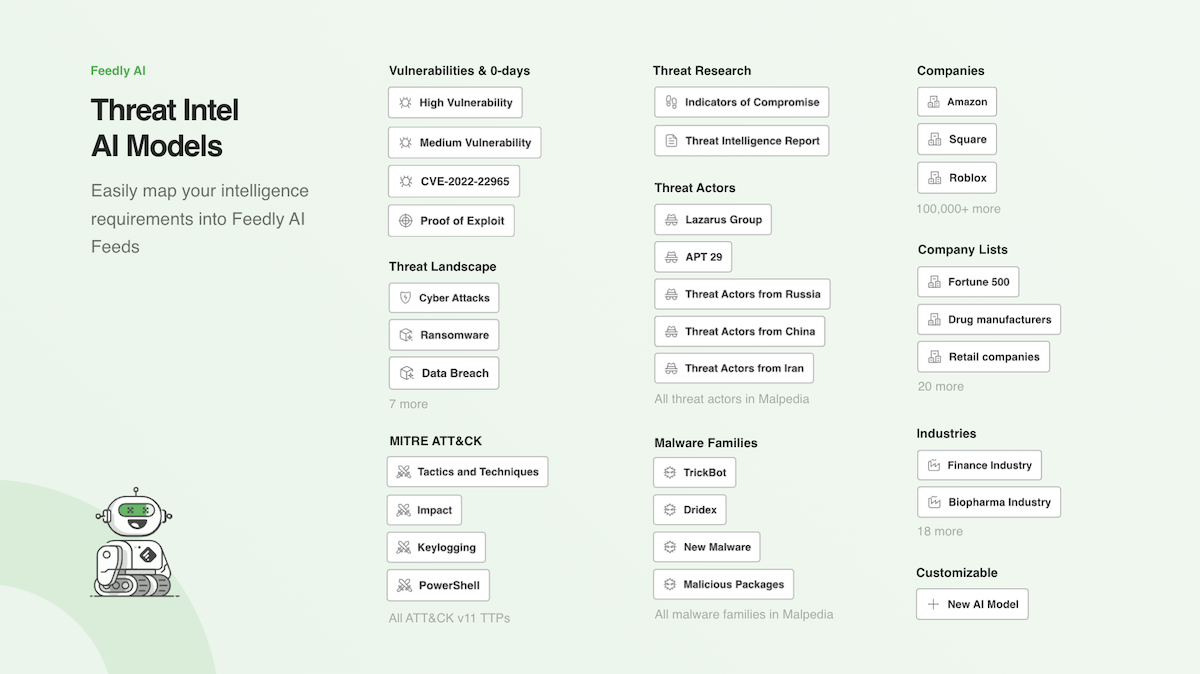
Let’s see how we can combine these AI Models to proactively track specific threats and stay one step ahead of your adversaries.
Tracking the behavior of threat actors and malware families can be tedious and overwhelming, taking up valuable time that could be spent hunting for malicious activity in your environment.
That’s why Feedly has created a set of AI Models that automatically tag threat actors, malware families, TTPs, and IoCs.
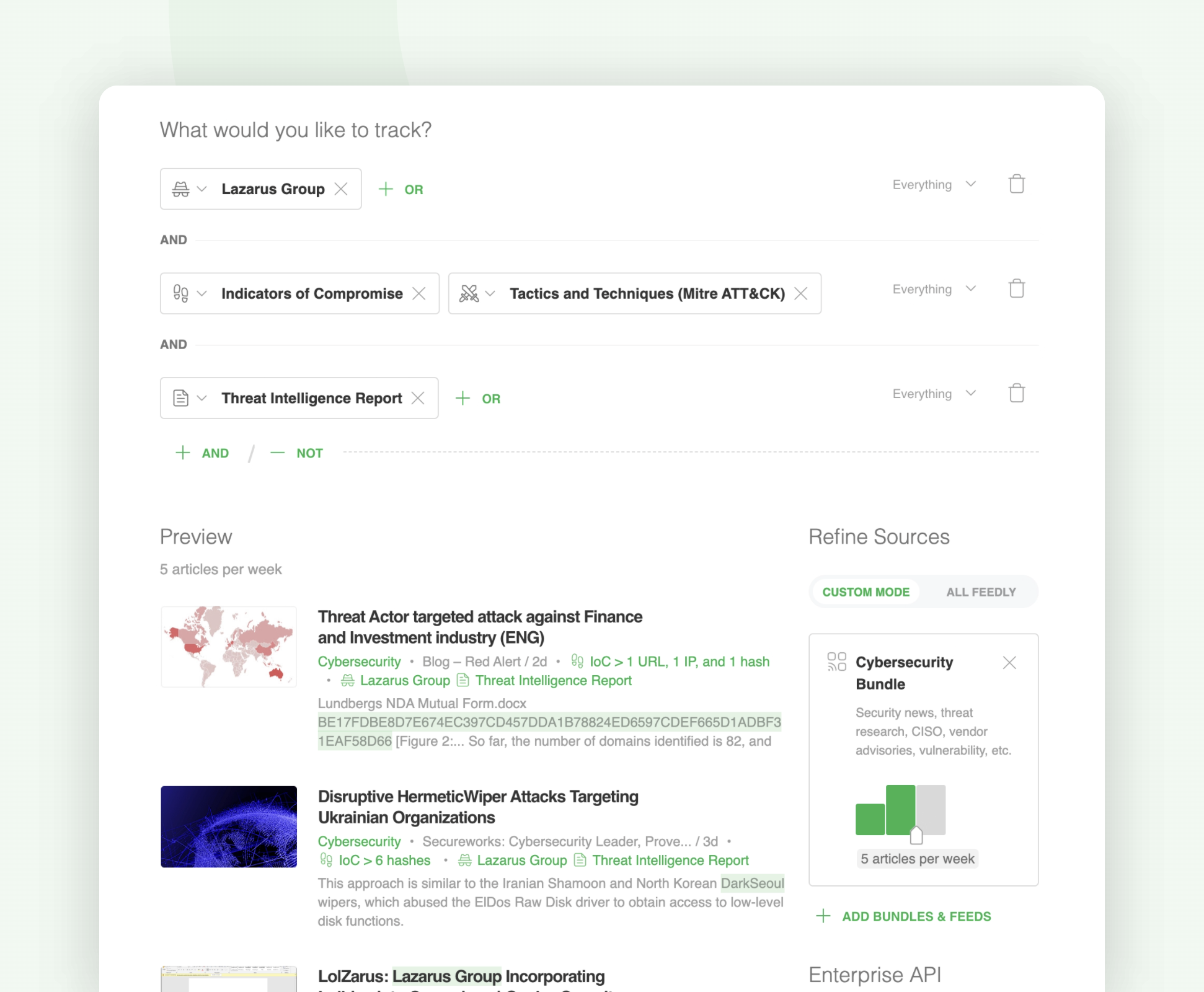
Let’s take a look at an AI Feed designed to track the latest IoCs and TTPs related to Lazarus Group across threat intelligence reports published on the web:
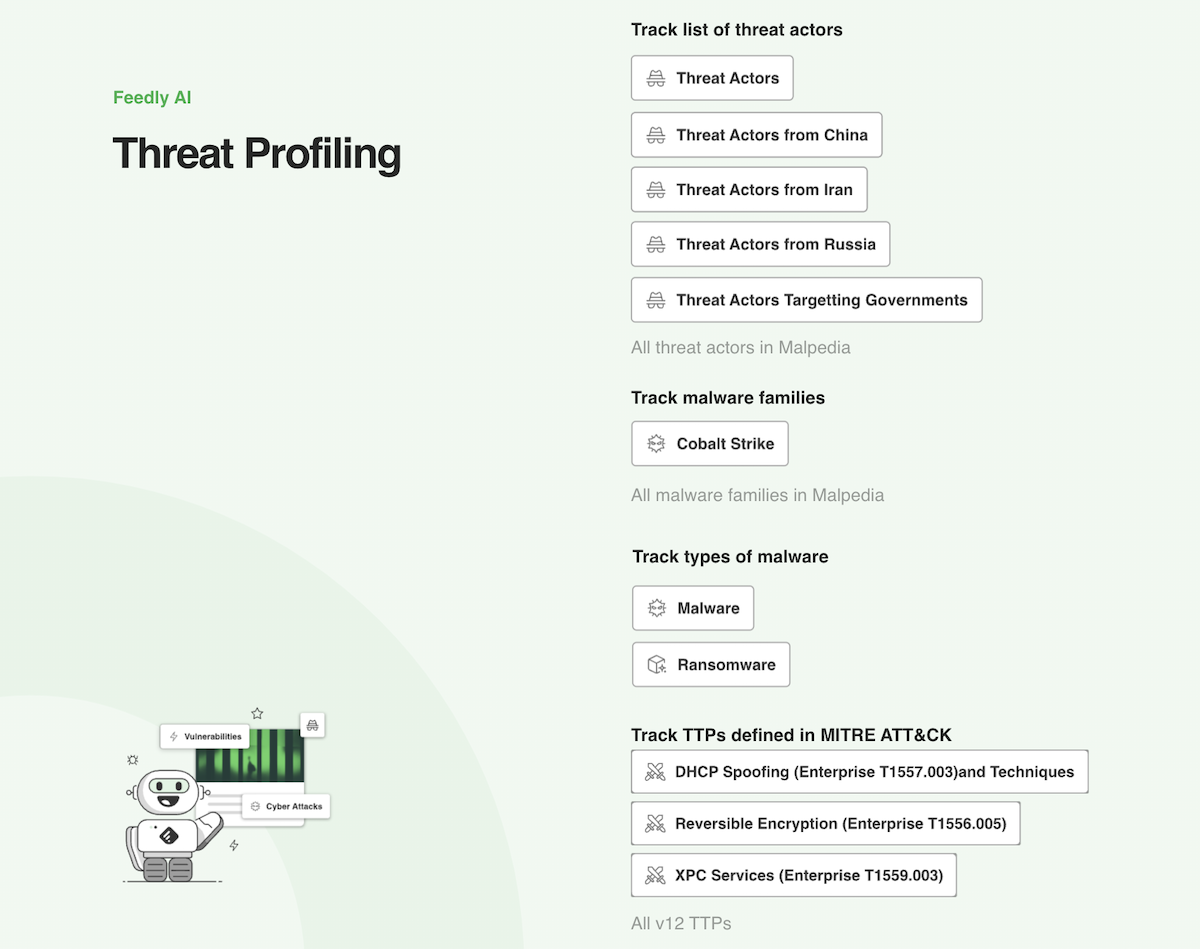
Here are some additional AI Models you can use to broaden or narrow your threat profiling:
Staying up to date with the latest attacks against your industry can help you be better prepared when putting defenses in place, as well as help you learn about which threat actors to look out for so you can be more targeted when gathering intelligence.
Let’s take a look at an AI Feed designed to gather intelligence about cyber attacks in the finance industry:
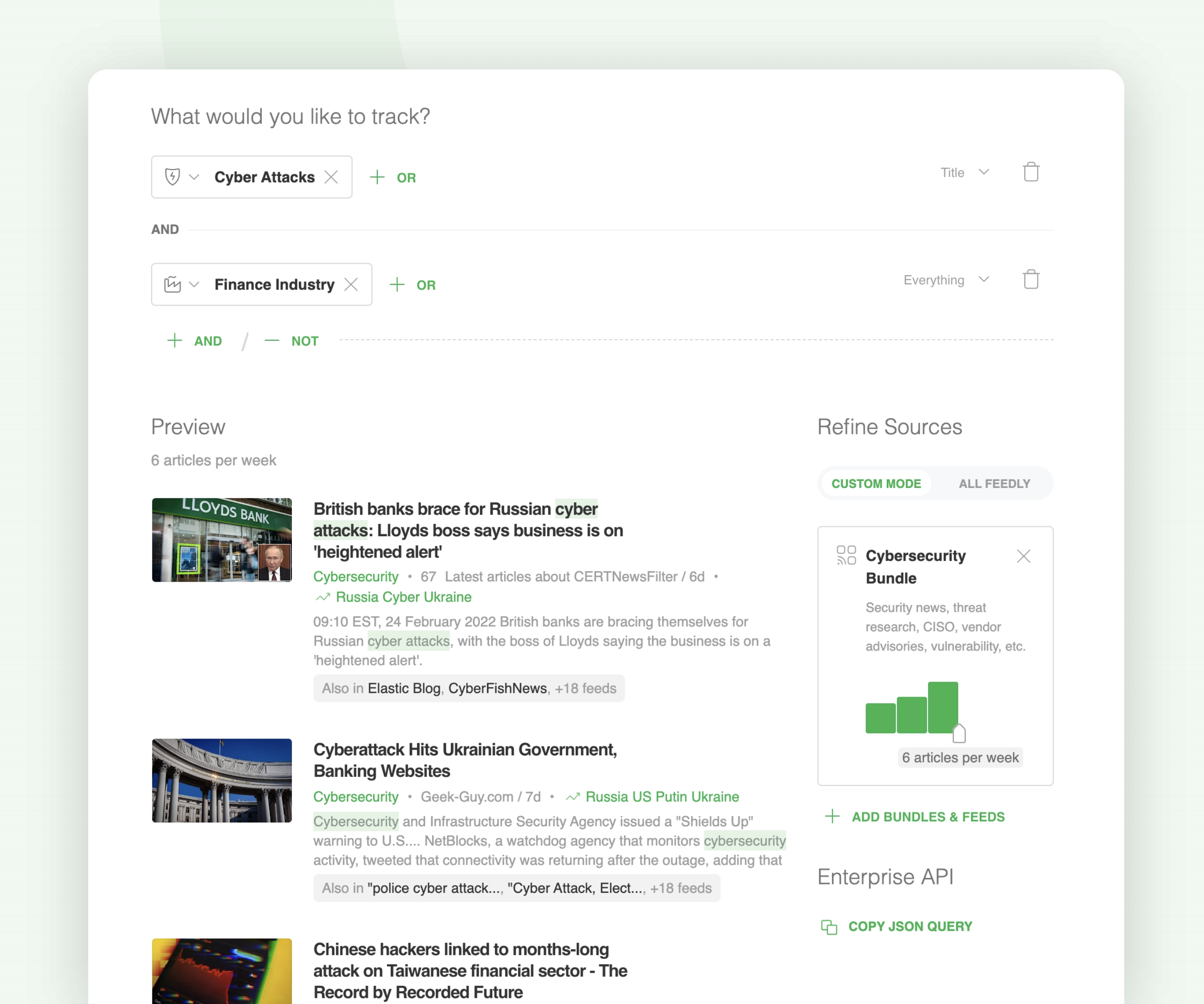
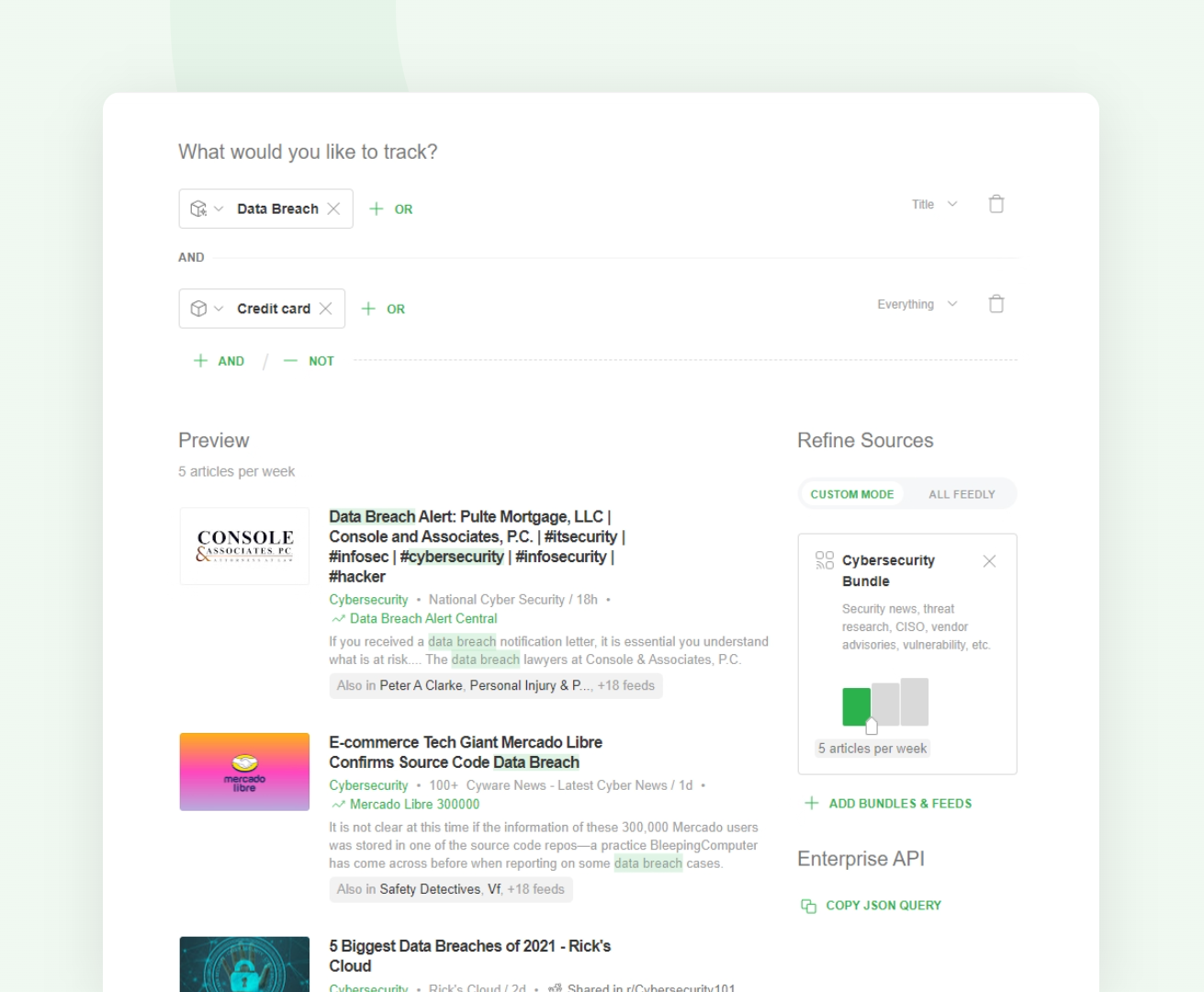
You can also easily narrow your focus on a specific type of attack:
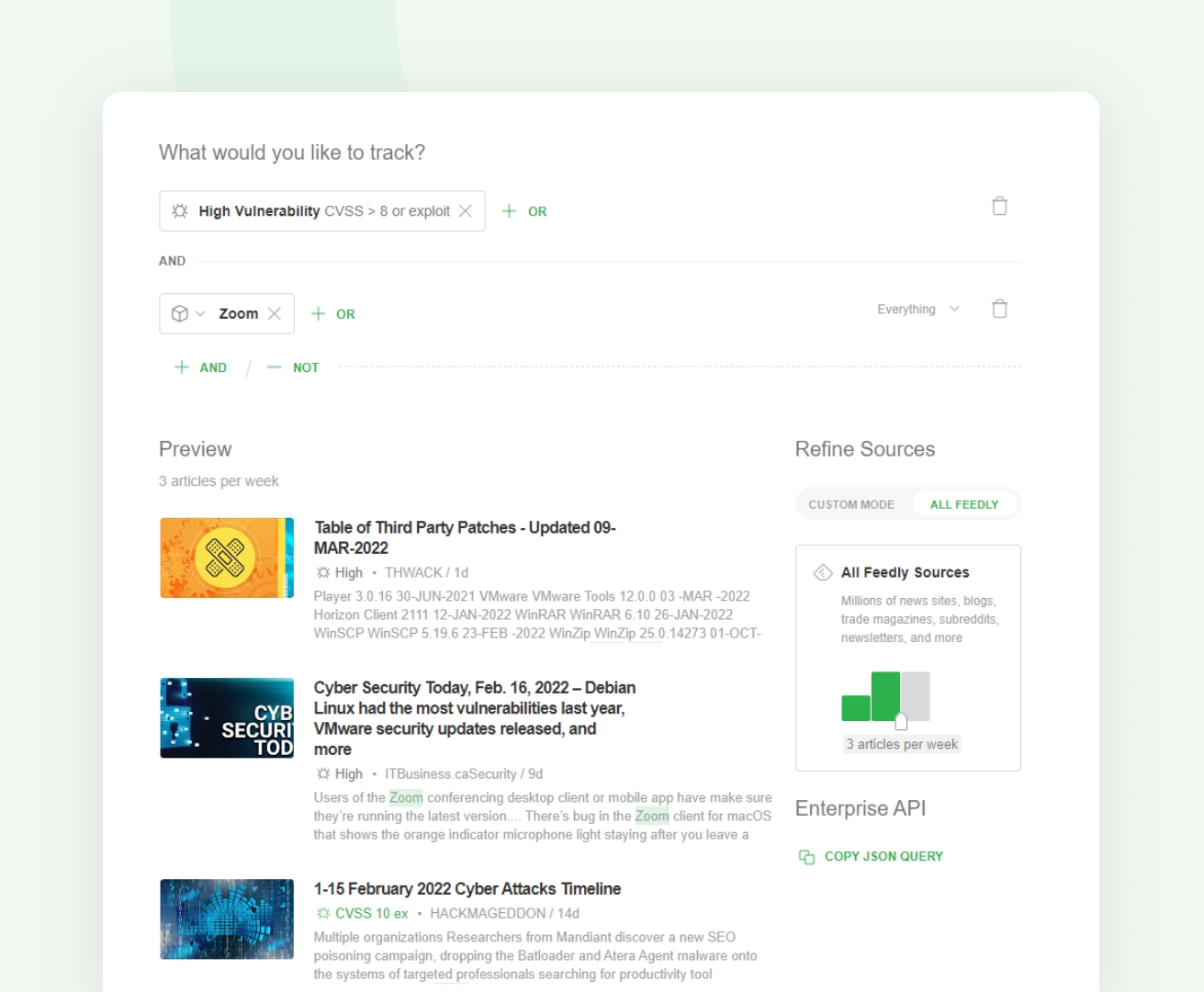
Manually keeping ahead of new vulnerabilities and zero-days is an impossible task, but you can set up AI Feeds to help you stay up to date on new vulnerabilities that come across the radar of the global cybersecurity community.
Feedly aggregates vulnerability information from NVD and over 20 vendor advisory sites — as well as monitoring many sources to find exploits for each CVE — in near real-time.
Let’s take a look at an AI Feed designed to surface critical vulnerabilities and zero-days related to a vendor deployed in your environment:
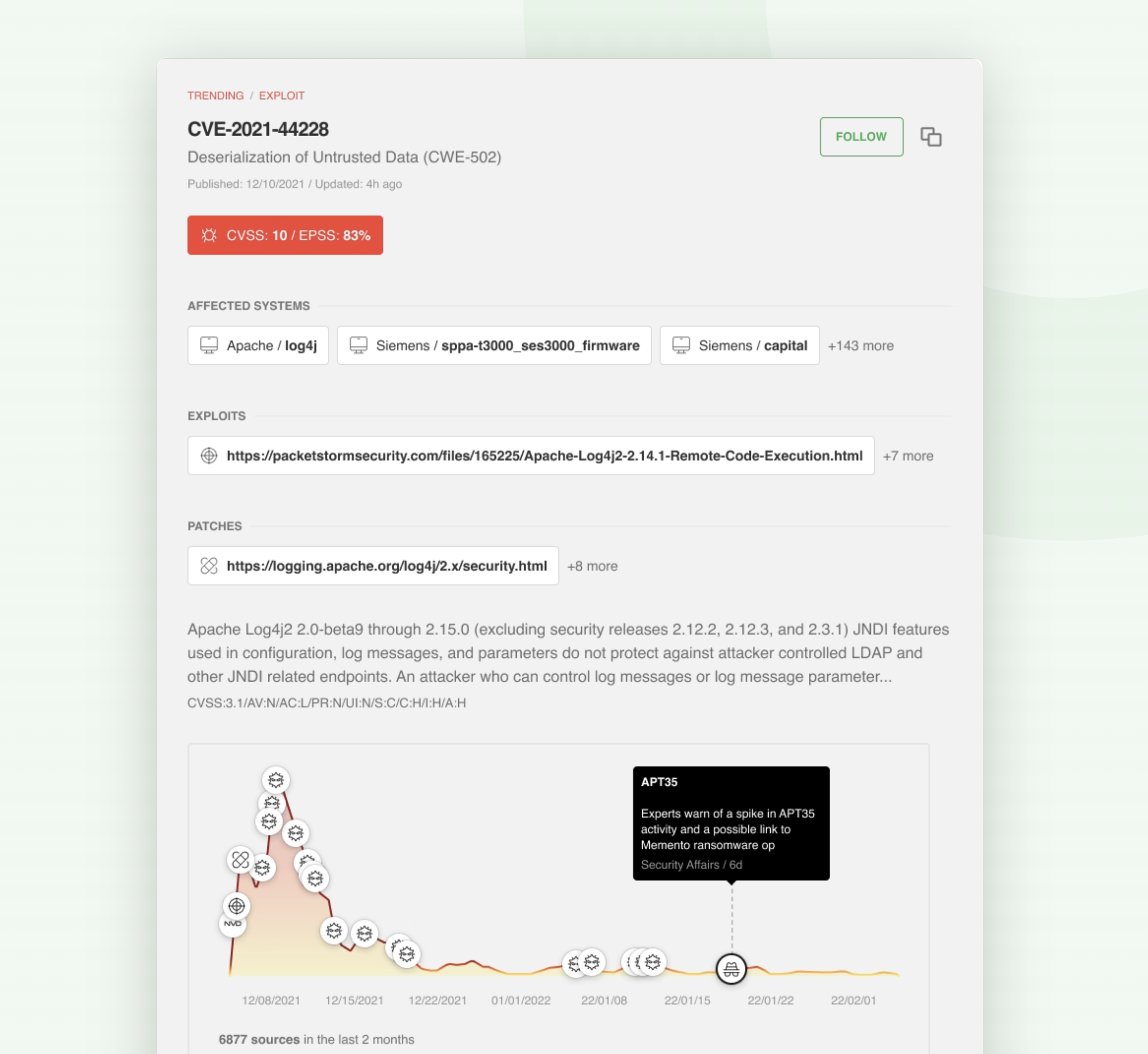
When you discover a new CVE, you can use the CVE insights card to get a 360 degree view of that vulnerability and decide if you should create a ticket for your response team.
You can also use AI Feeds to track niche cybersecurity topics.
Let’s take a look at an AI Feed designed to gather intelligence about malicious, compromised, or hijacked packages:
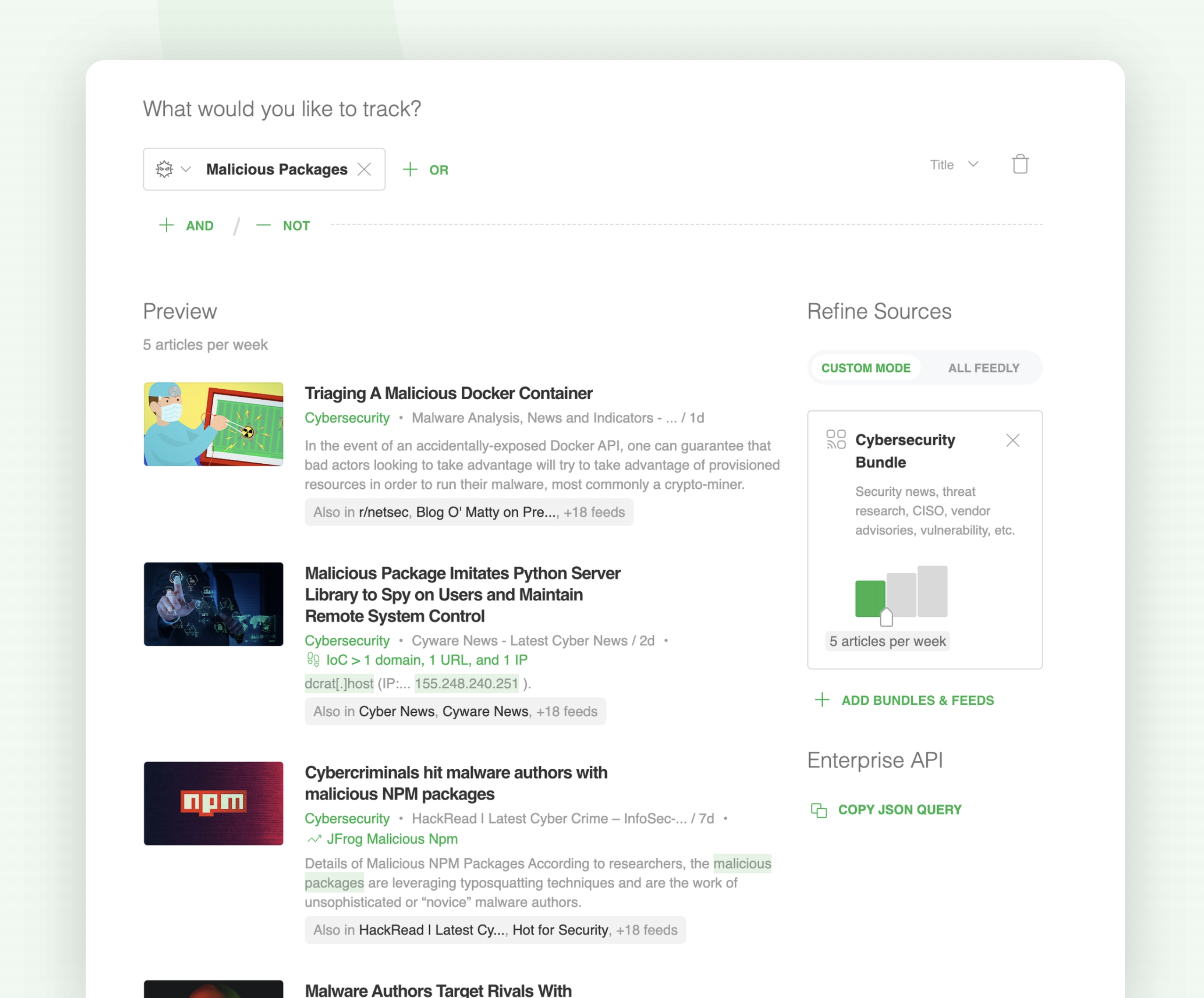
Here are some additional AI Models you can use to track niche cybersecurity topics:
The world’s leading cybersecurity teams use Feedly for their OSINT, so the product constantly improves based on their feedback.
Here is a roadmap of some of the new AI Models we are researching:

Feedly for Threat Intelligence customers can reach out to us at enterprise@feedly.com to give feedback on improving existing AI Models or creating new ones to ensure that Feedly is working at full capacity to serve your Threat Intelligence needs.
All of these features, plus many more, are available as a part of Feedly for Threat Intelligence. To learn more about any of these features, or start a free 30-day trial, click the link below.

Looking to monitor a specific CVE ID? Previously, you had to type in the exact CVE ID and be sure it was the right number. Now, Feedly AI autocompletes the CVE ID and shows you the description of the vulnerability, so you can be sure you’re tracking the right one.
This is a small improvement to the UI that makes it much easier for you to quickly track a CVE (instead of entering the ID manually) and to make sure you’re tracking the right CVE.
The more high profile a CVE becomes, the more likely threat actors will develop exploits for it. You can keep an eye on a trending vulnerability by simply creating an AI Feed and adding it to your “Trending vulnerabilities” Folder, for example.
When it’s taking a while to apply a security patch, you want to keep an eye on the tactics used to exploit the vulnerability. Create an AI Feed for the CVE ID and the model “Cyber Attacks” and Feedly AI will look for attacks or exploitation attempts related to the specific CVE.
Then, you and your team can use this information about available exploits to prioritize which vulnerabilities to patch. You can also update the AI Feeds to add more CVEs if needed, like when a vulnerability has multiple IDs associated with it.

Tracking, gathering and ingesting indicators of compromise is a great way to proactively hunt for signs of an attack on your environment. Since Feedly AI allows you to gather and export IoCs from multiple sources (including articles, Twitter, Reddit, and emails), you can create an AI Feed to track a specific CVE ID and the “Indicators of Compromise” AI Model.
Once you create an AI Feed for IoCs related to the specific CVE you’re tracking you can easily export the resulting IoCs with context and add them to your own security environment.
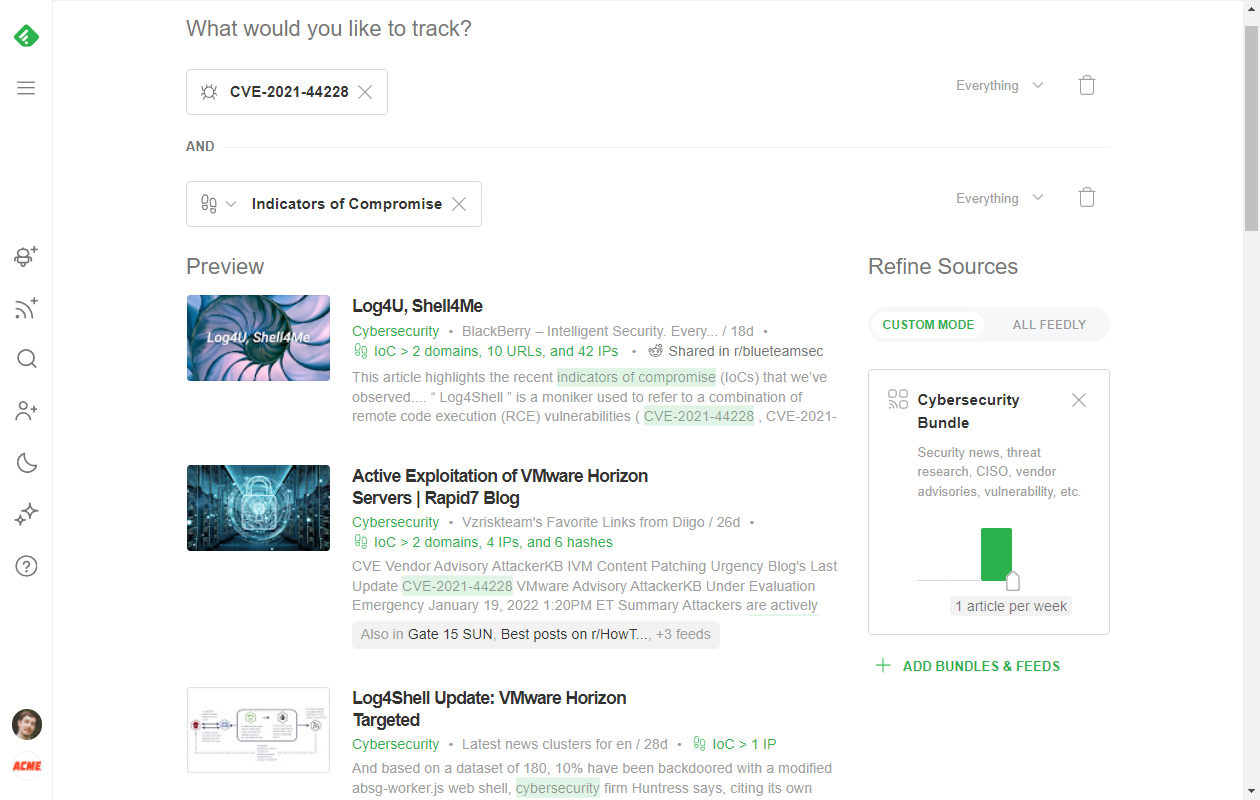
Gather intelligence others have curated by adding the “Threat Intelligence Report” AI Model to your Web Alert. When you combine the CVE ID with the Threat Intelligence Report AI Model, you’ll get Threat Intel Reports mentioning the CVE.
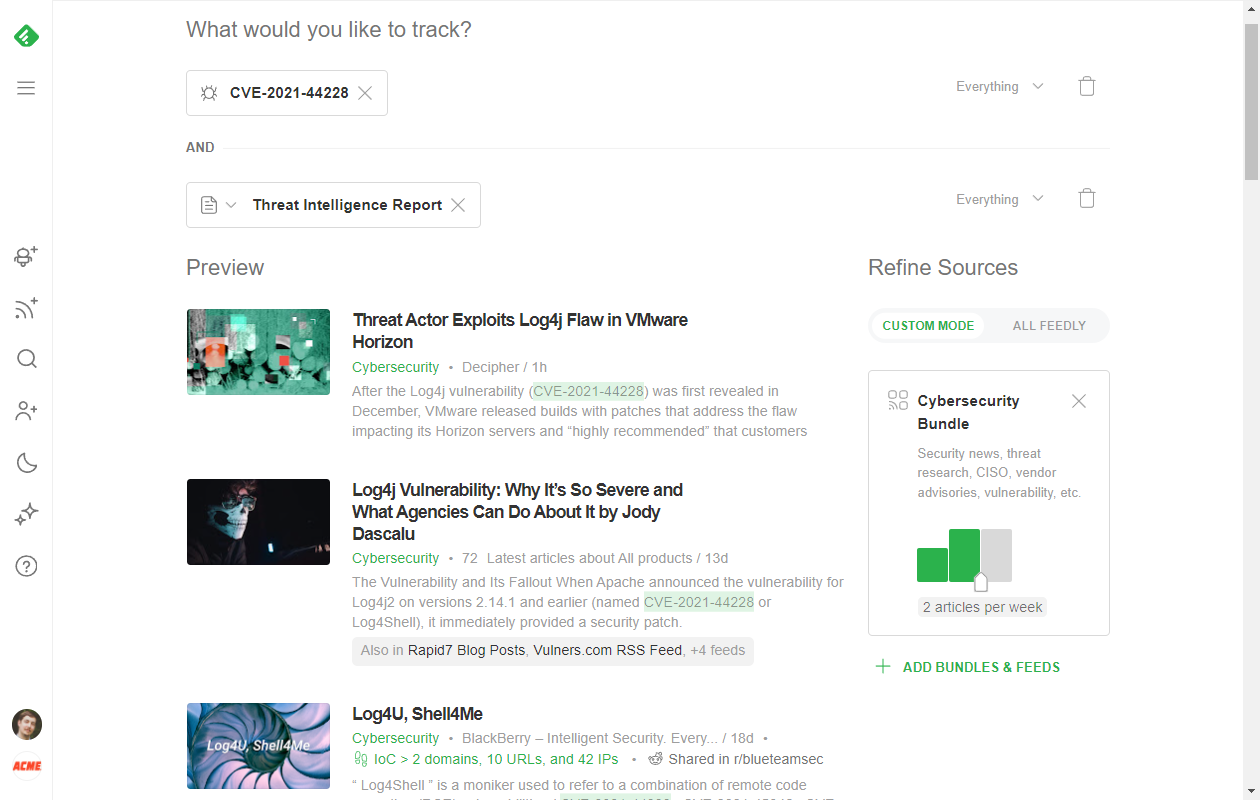
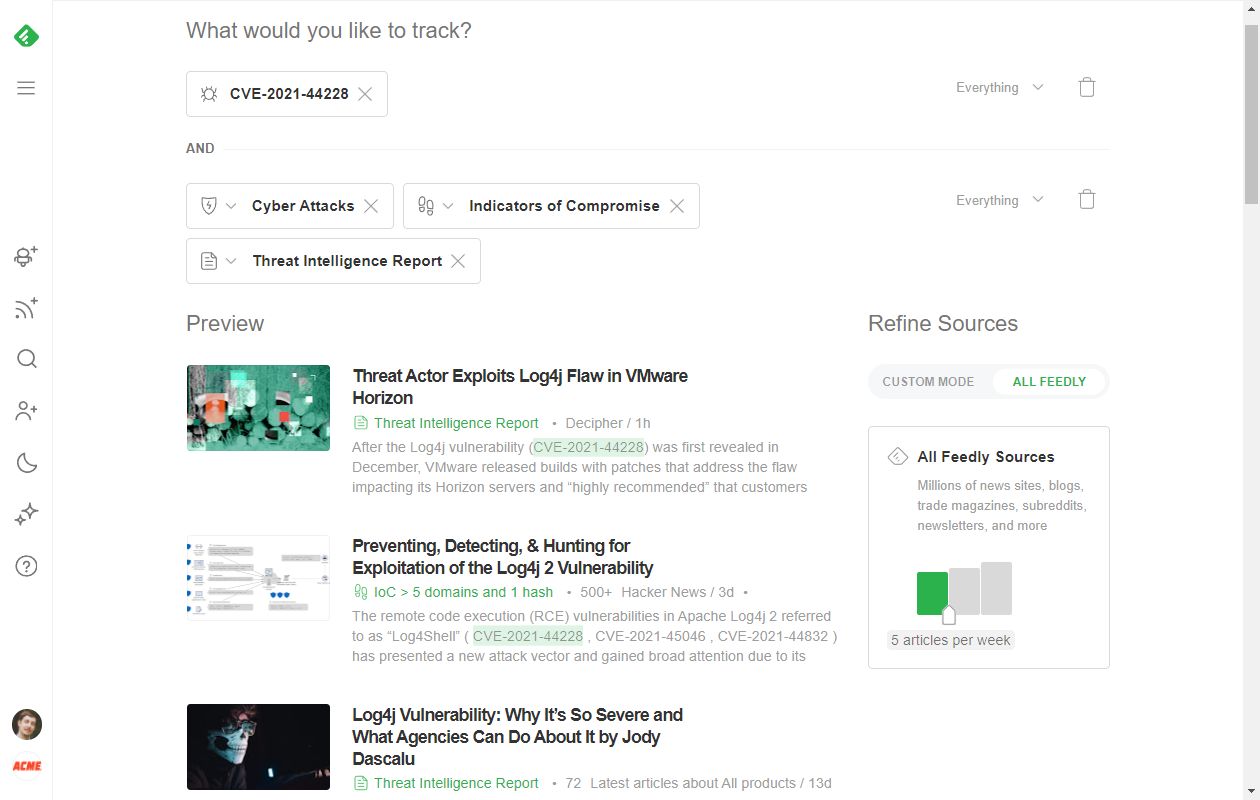
And if you want to get all angles of a CVE, you can combine all of these models into a single AI Feed. Just track the specific CVE ID and add other AI Models like Indicators of Compromise, Threat Intelligence Reports, and Cyber Attacks.
And don’t forget — to get a complete overview of a specific CVE in the moment, you can also click on the CVE ID and open up the CVE Insights Card. You’ll find an at-a-glance overview of exploits, malware families, and related threat actors in a single view.
Not a member of the Feedly for Threat Intelligence community yet? Try a free 30 day trial and speed up your discovery and research of emerging threats.

How to structure your Feedly for Threat Intelligence account to optimize your open source threat intelligenc
Contextualized CVE information for faster threat research, without the overwhel

Many of the leading cyber security teams use Feedly to organize and automate their open-source threat intelligence and stay ahead of emerging threats. We have had the chance to research 100 of them and review their open-source threat intelligence best practices.
In this article, we will share how they translate their intelligence needs into various types of feeds and how they structure those feeds into a highly functional Feedly account.
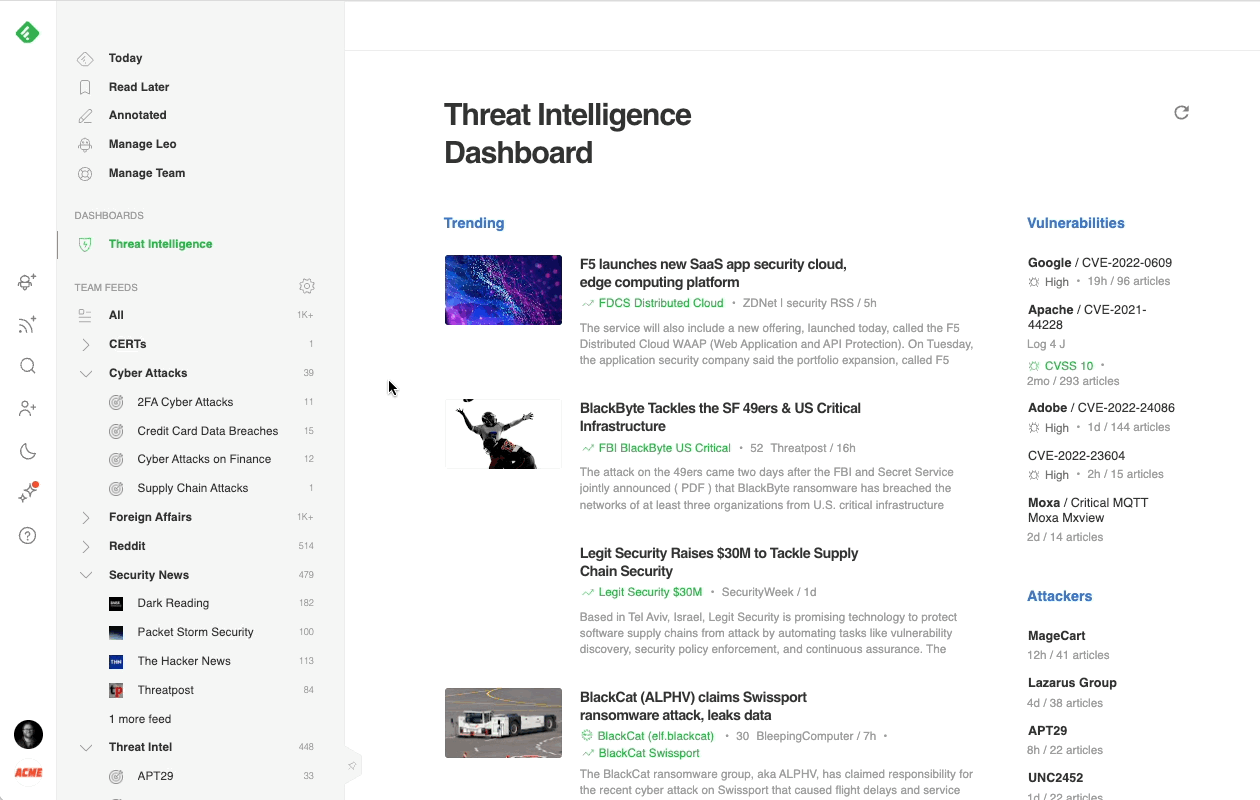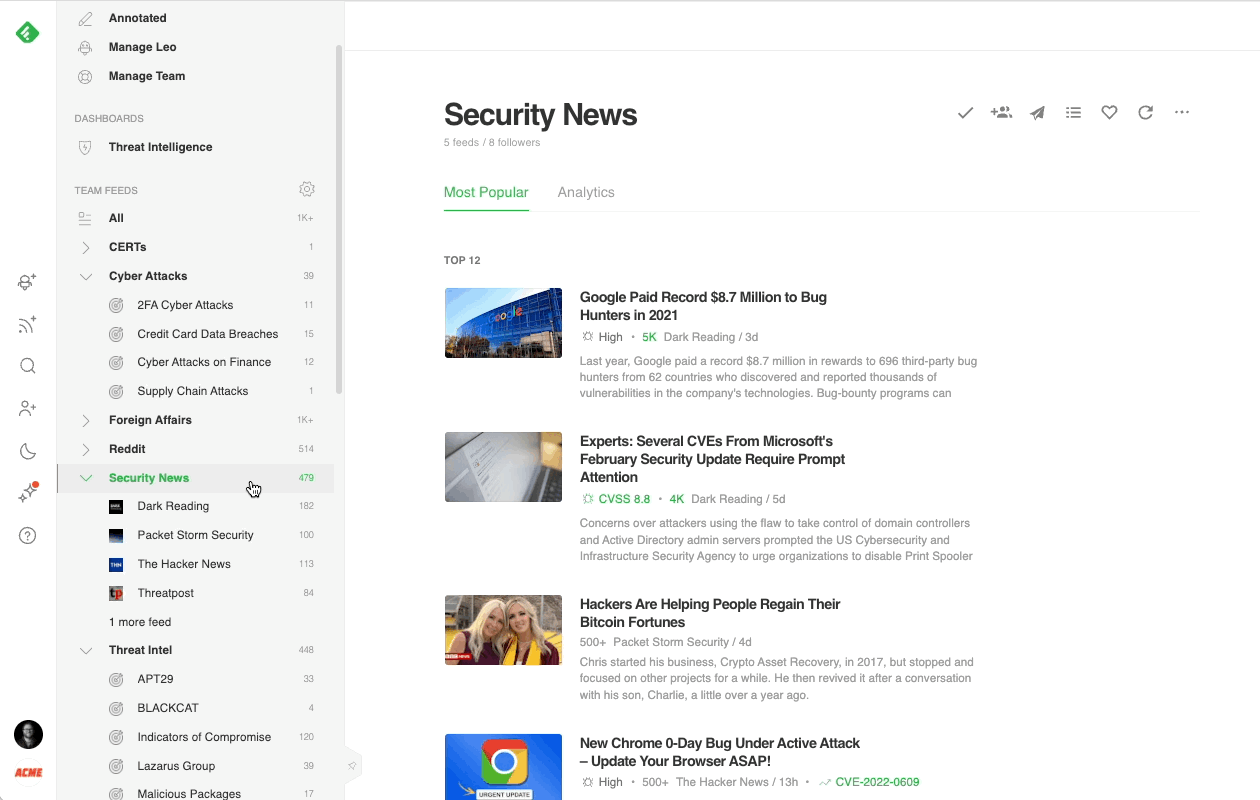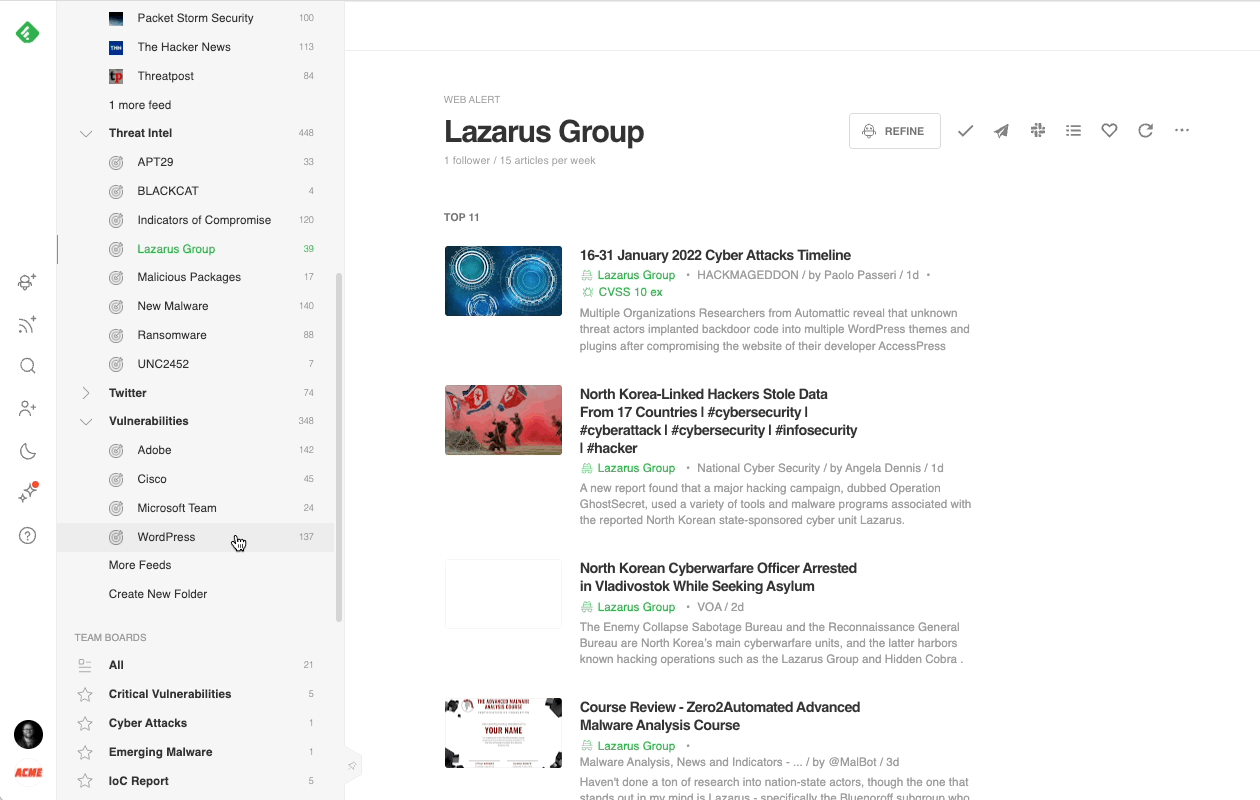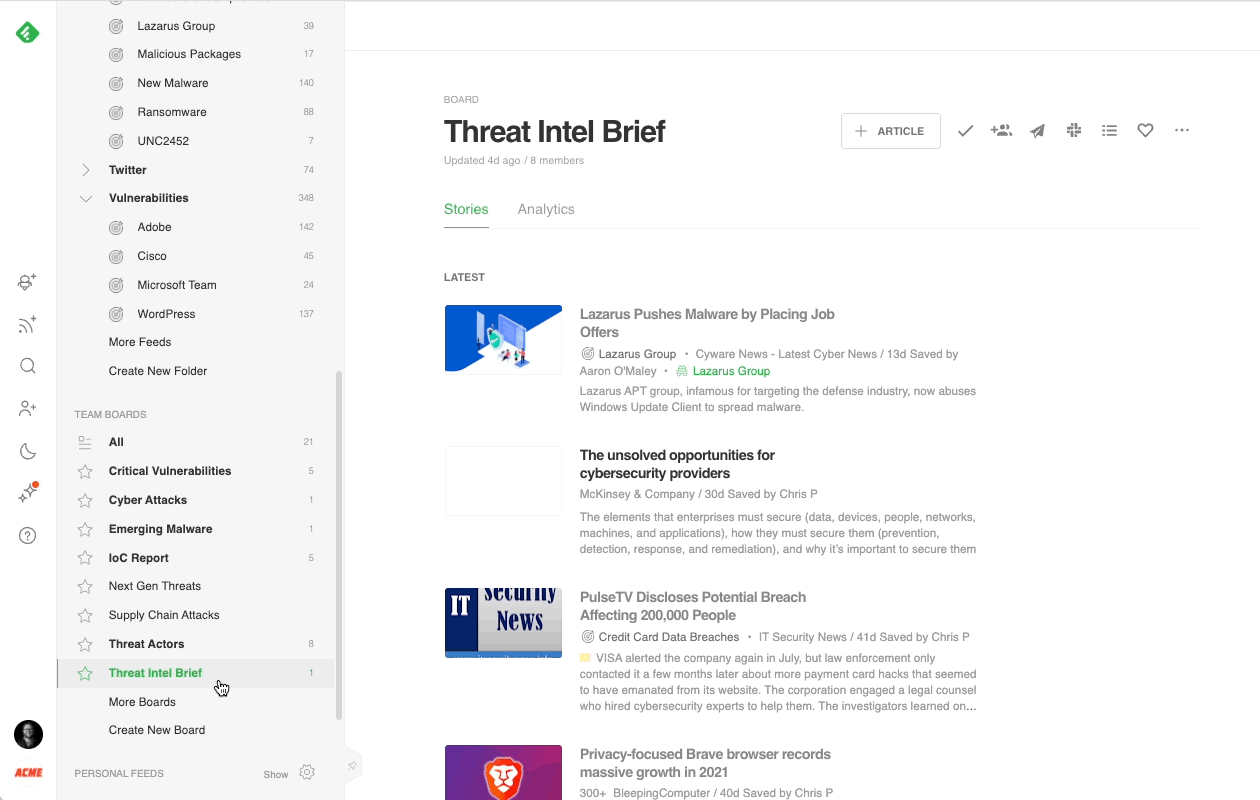
Most cybersecurity professionals start their day in the Threat Intelligence Dashboard. It offers a broad overview of the emerging threat landscape: trending cybersecurity articles and attacks, new critical vulnerabilities, active attackers, new behaviors, and malware families, so it’s easy to get a sense of what’s going on in just a few minutes.
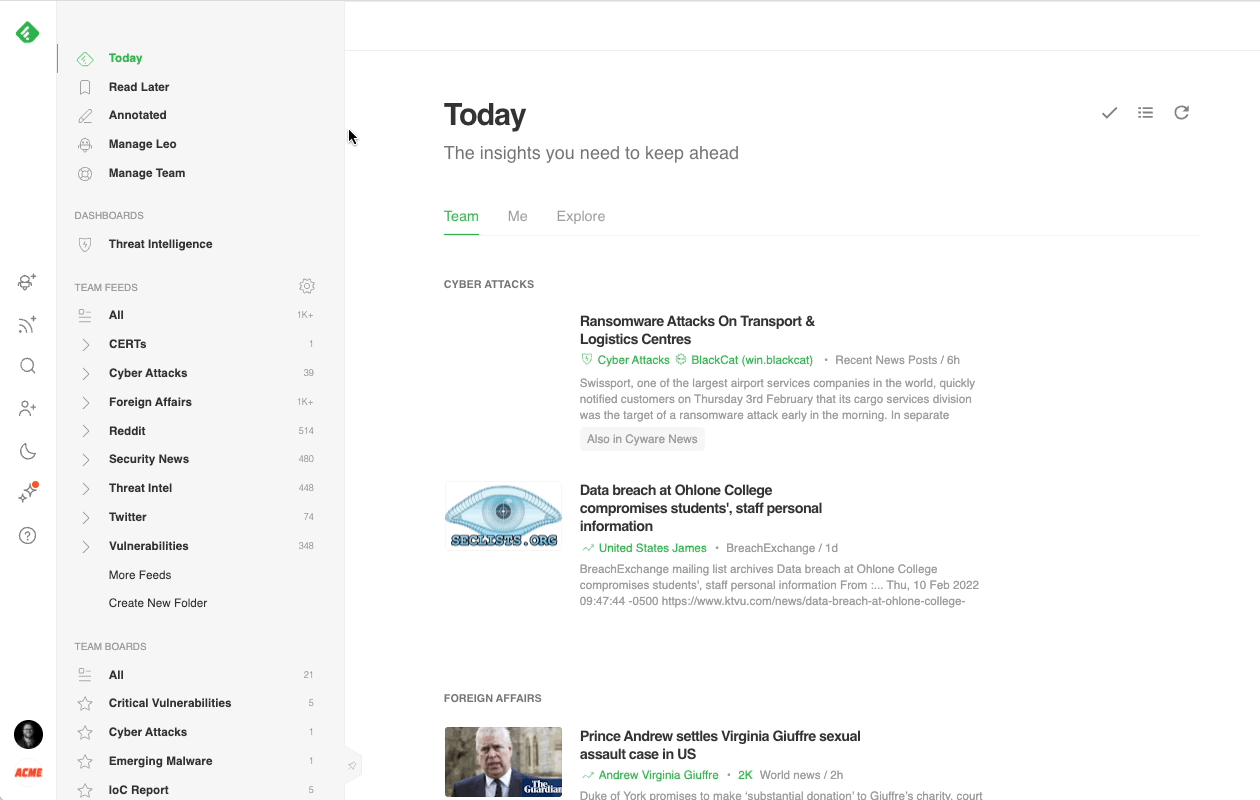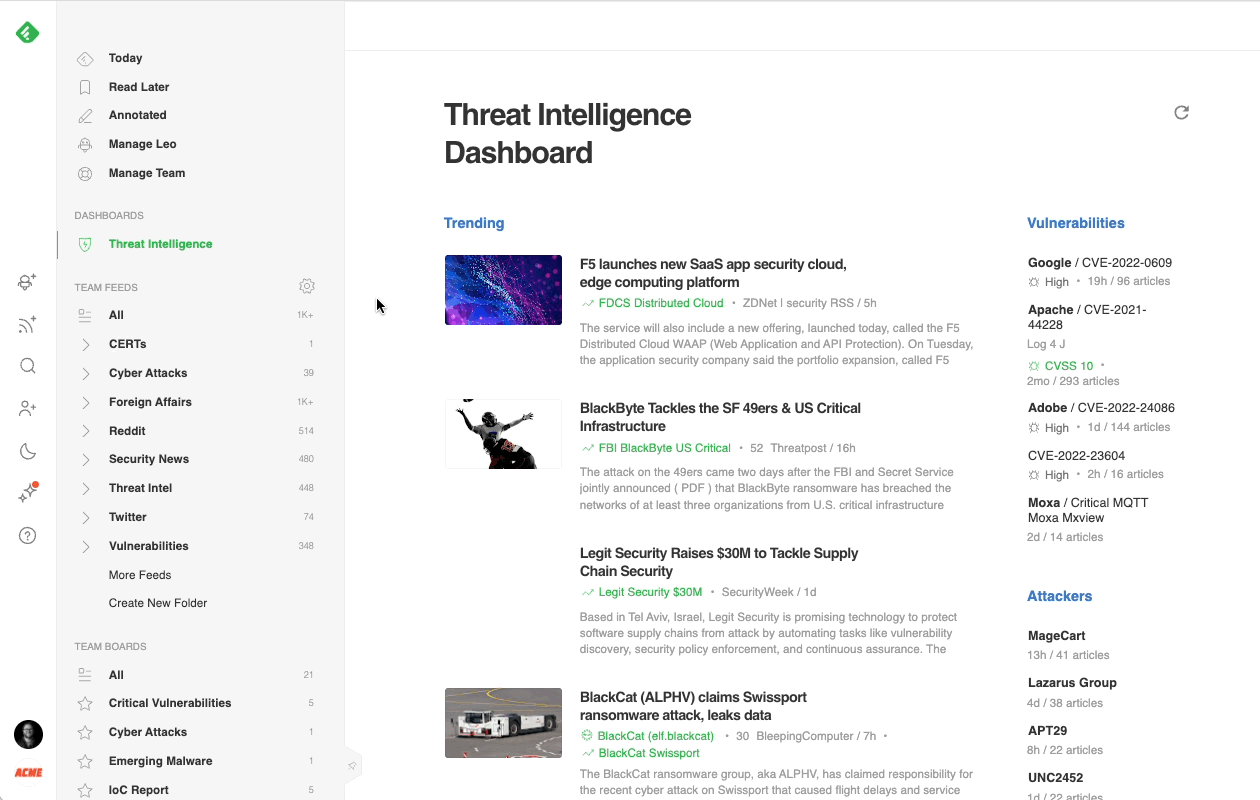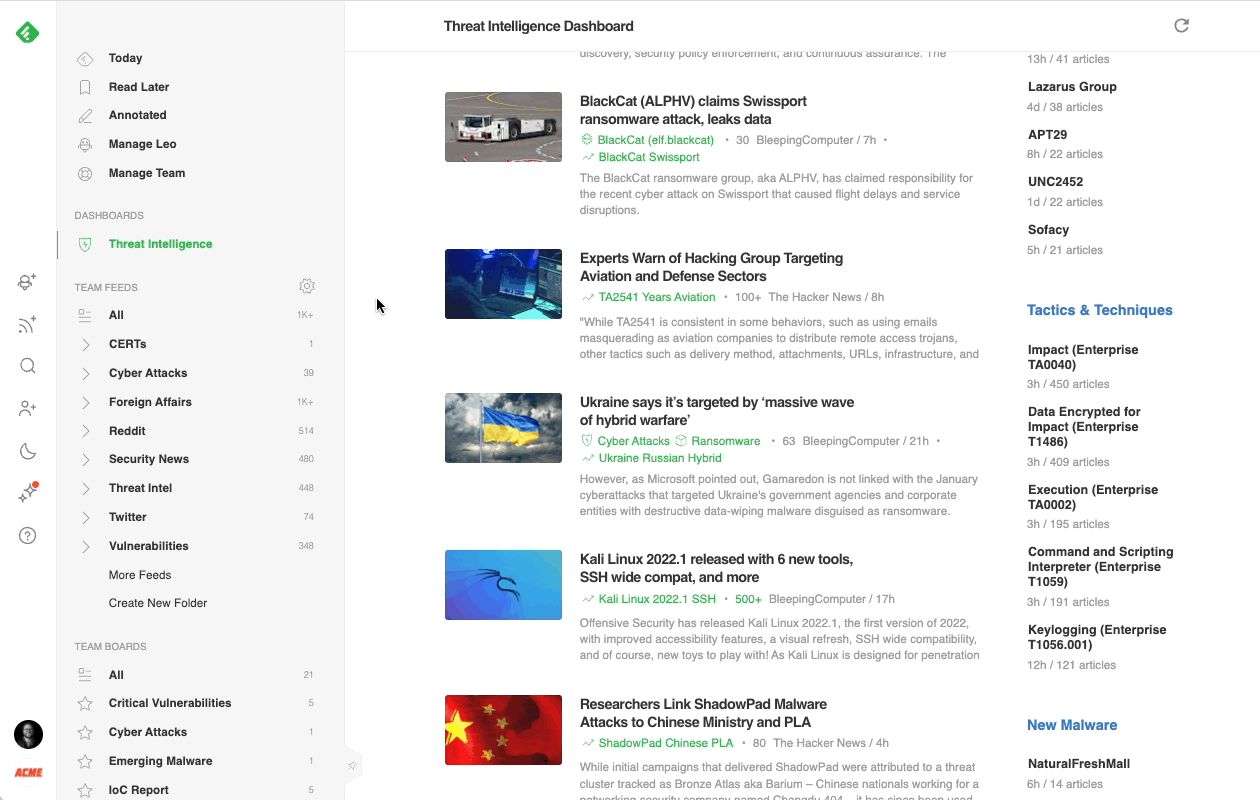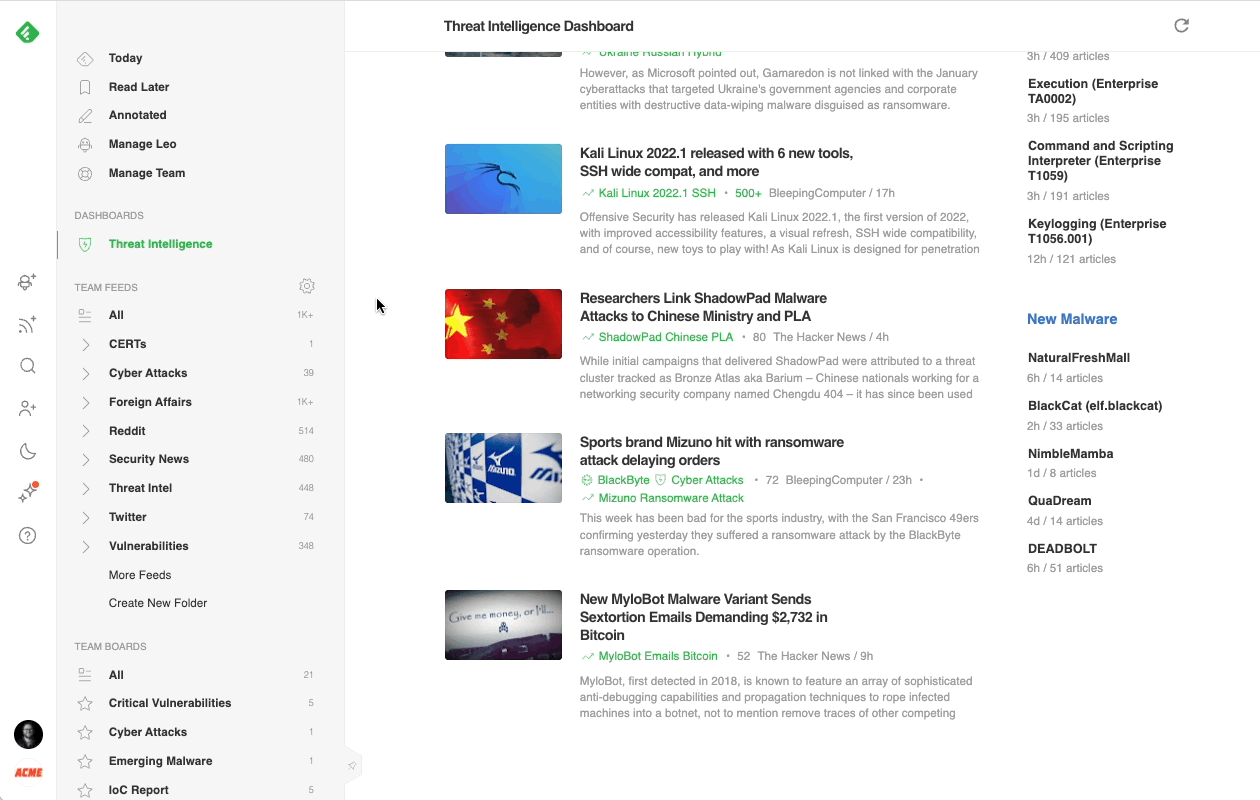
Here’s a brief overview of each section:
The most effective way to track critical vulnerabilities and zero-days across the web is with Feedly AI. Feedly AI has been pre-trained to understand vulnerabilities and assess their severity. It reads millions of articles every day, looking for critical security threats.
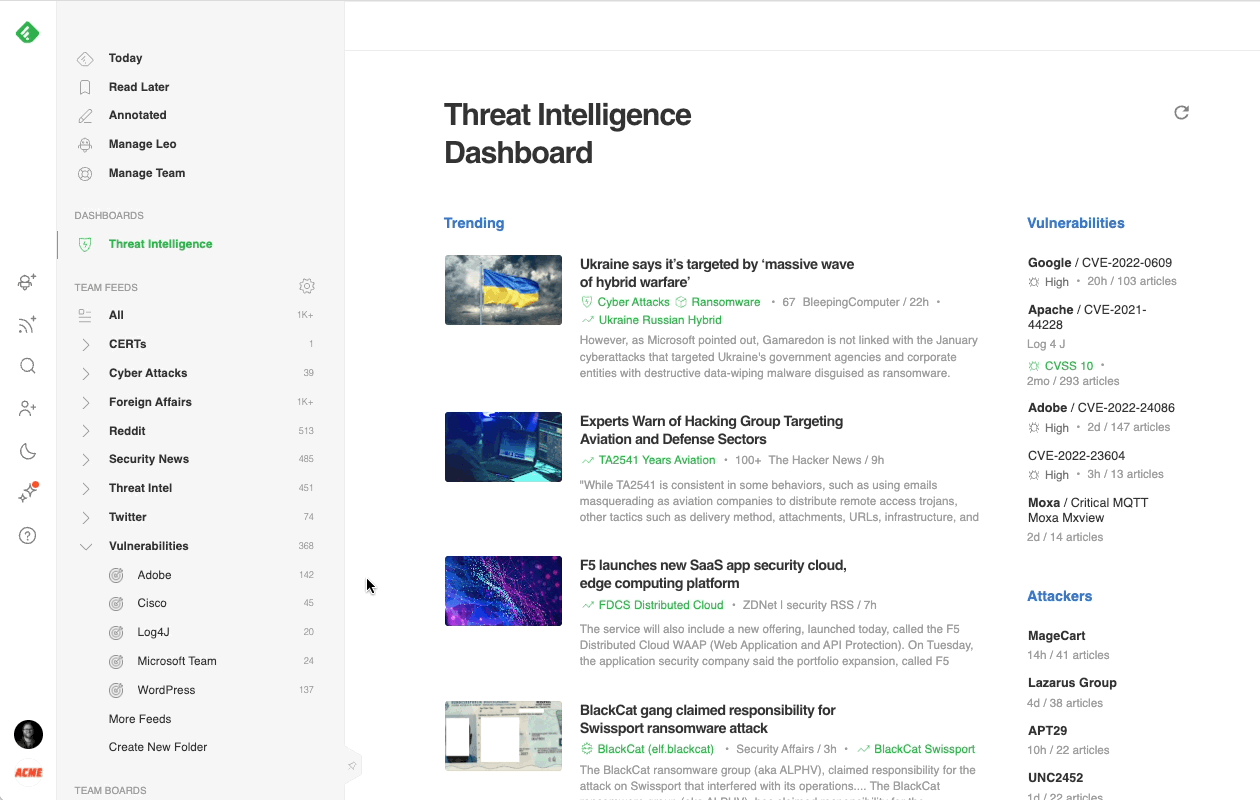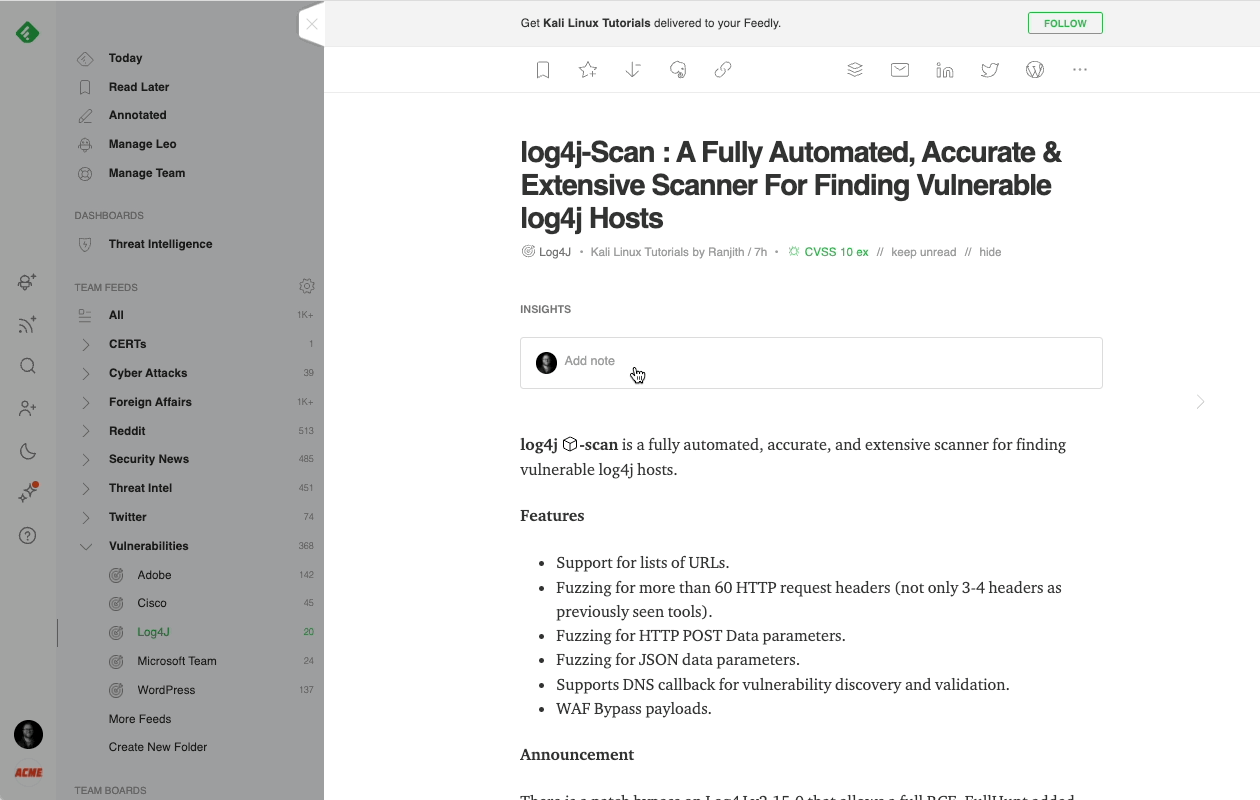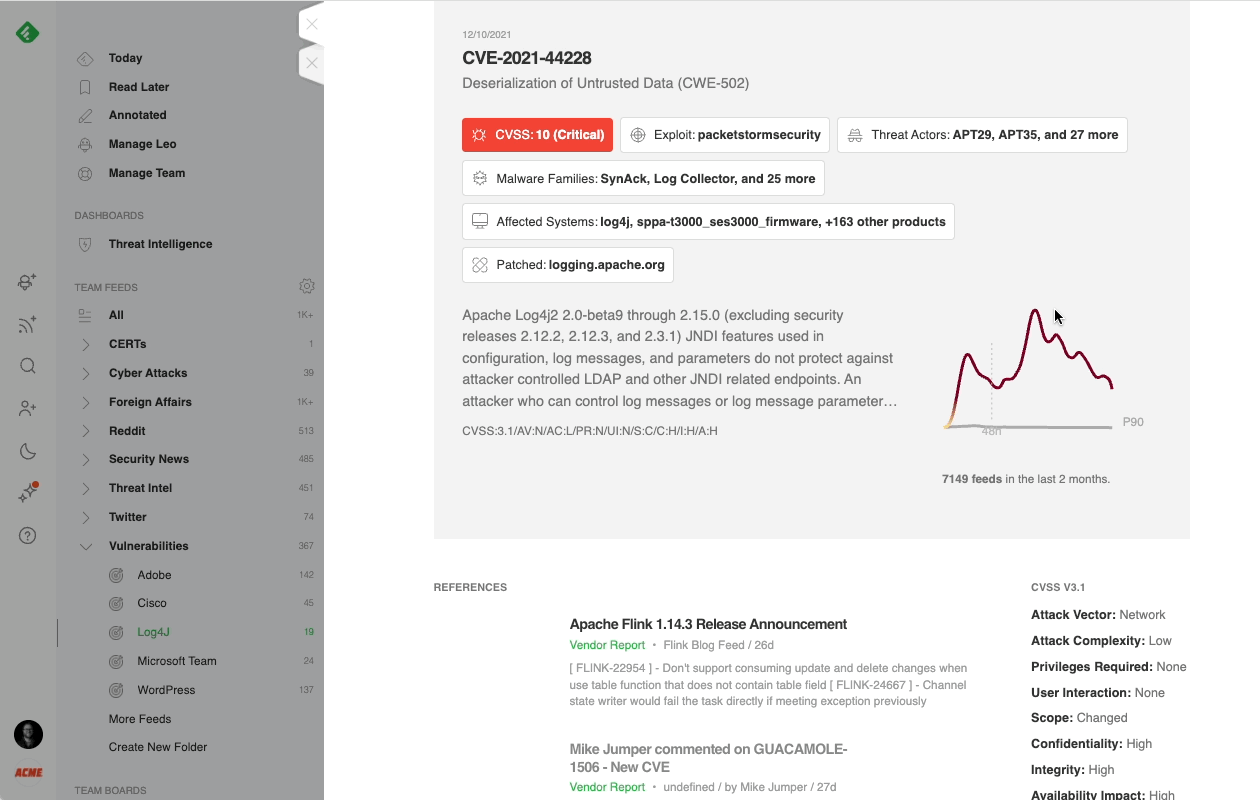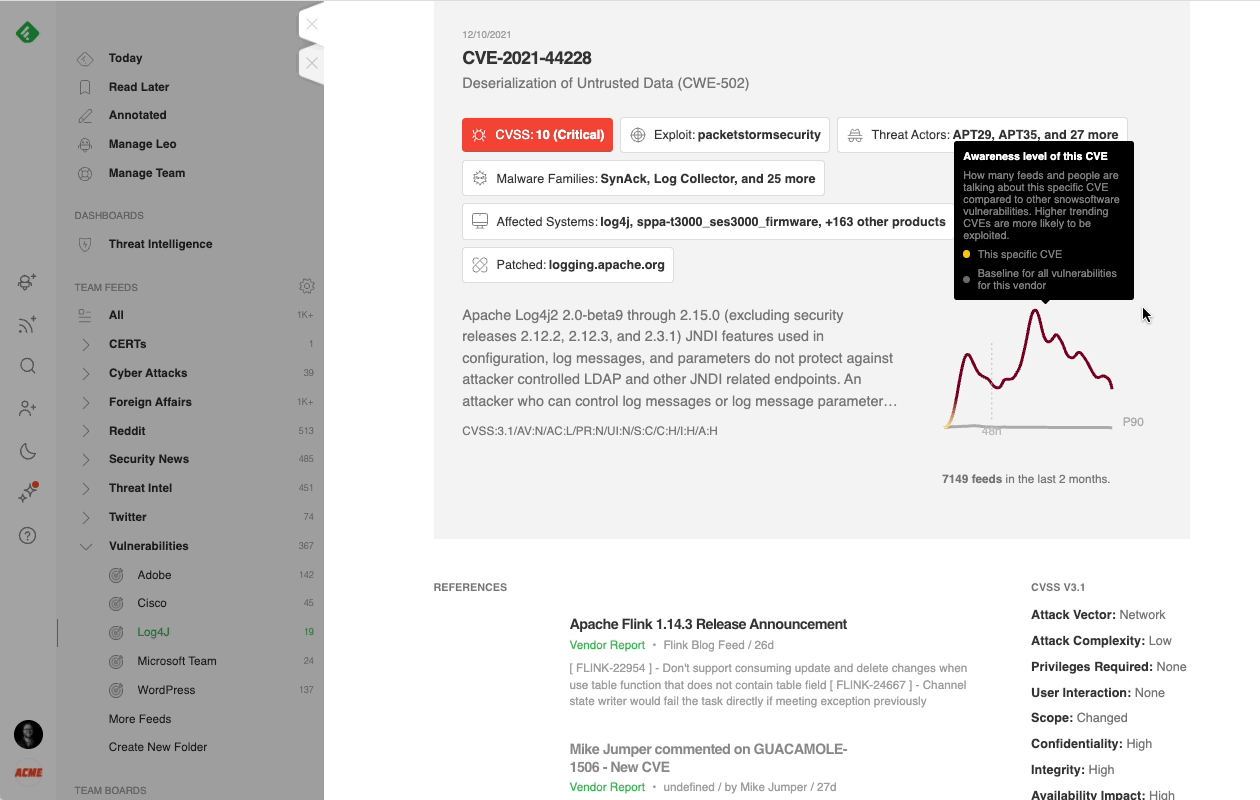
When Feedly AI finds a CVE, it automatically searches for its CVSS score, related exploits and malware families, links to threat actors, CWE information, and patches. It then organizes all this information into a rich CVE insights card.
If the CVE doesn’t have a CVSS score yet, Feedly AI uses machine learning to predict the CVSS score, keeping you one step ahead of the latest emerging threats.
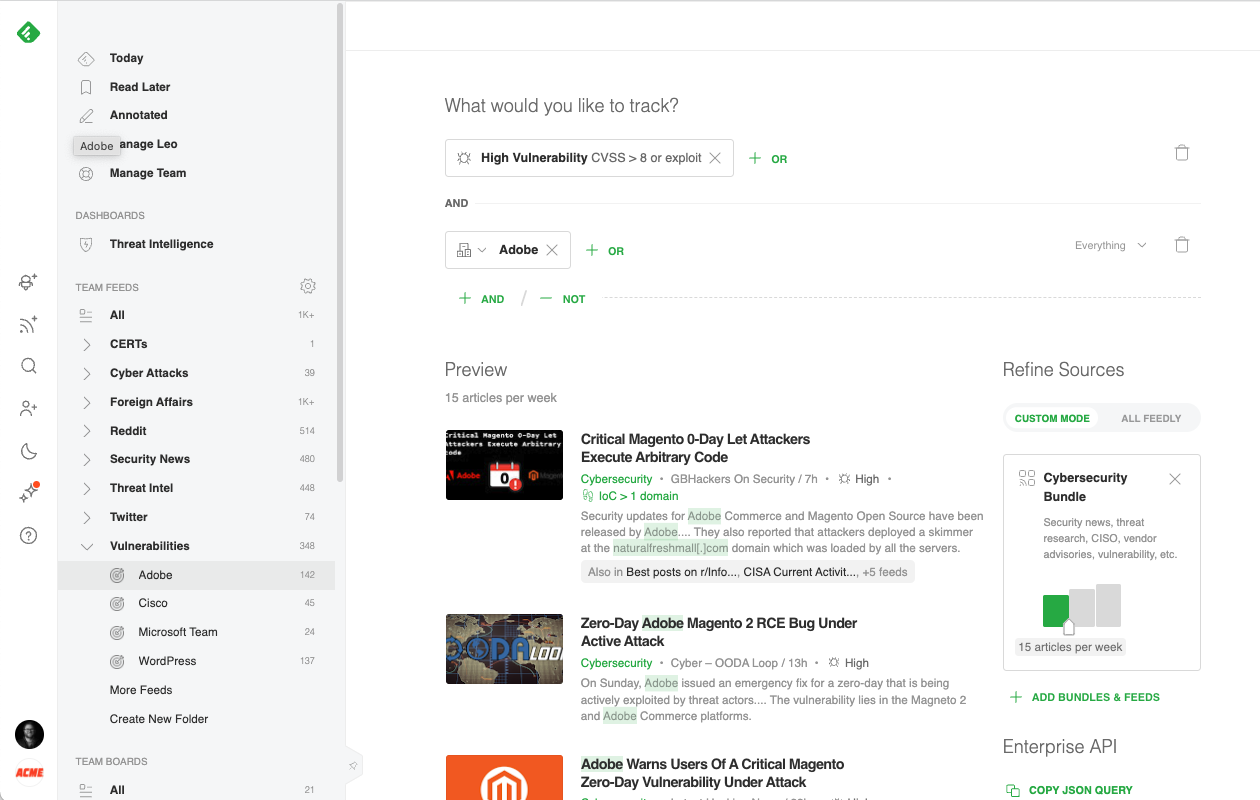
Creating a broad (Feedly) AI Feed targeting all critical vulnerabilities gives you a big picture view of what is happening across the threat landscape, while adding specific vendors to the search narrows the focus into more precise and manageable feeds.
Cybersecurity teams often create an AI Feed for each of the main products deployed in their environment and group them into a Vulnerabilities folder.
One way cybersecurity teams track and visualize the behaviors of specific Threat Actors and Malware Families is by using Feedly’s integration with the Mitre ATT&CK framework. Feedly AI has been pre-trained to understand threat actors (integration with Malpedia), Mitre ATT&CK (version 10), and the model of threat intelligence reports. These three models can be easily combined to track the behavior of selected adversaries.
Here is an example of an AI Feed surfacing all the threat intelligence reports mentioning the Lazarus Group threat actor:
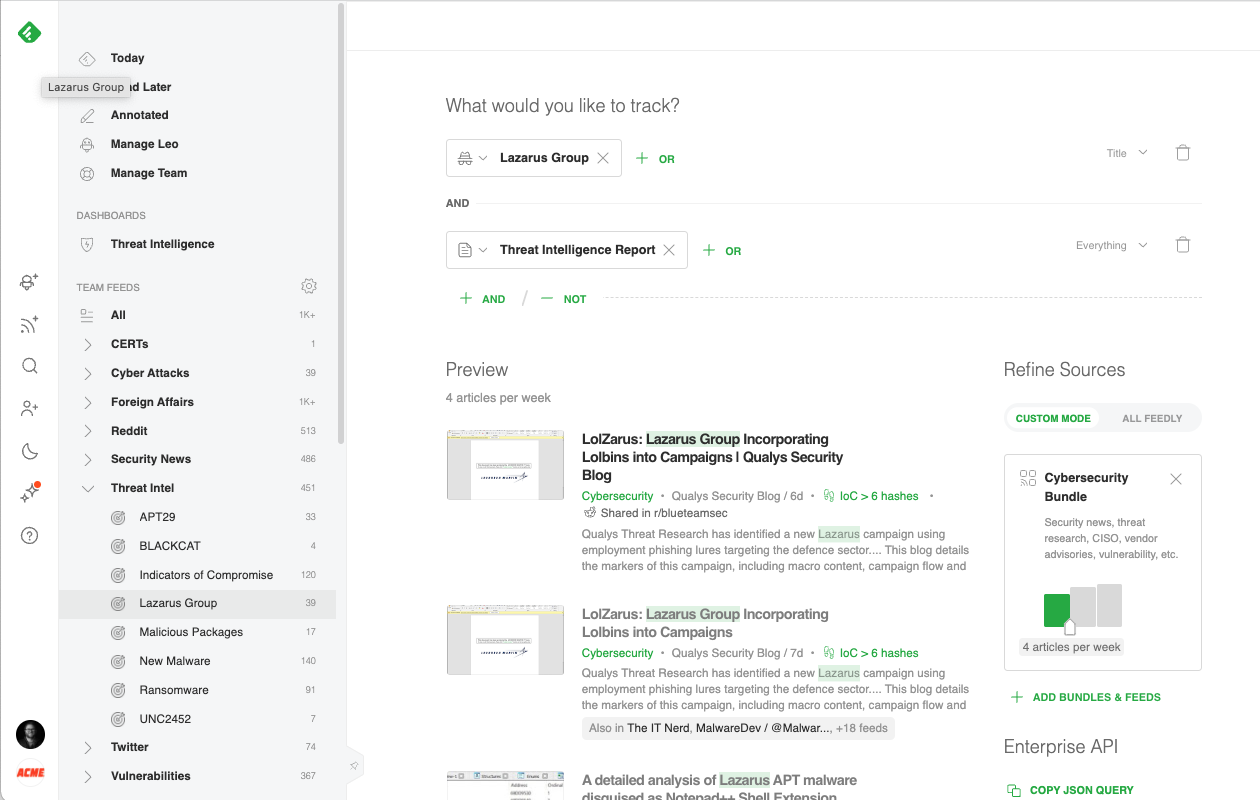
Cybersecurity teams often create an AI Feed for each of the threat actors and malware families defined on their threat profiling list and group them into a “Threat Intel” folder.
When Feedly AI finds an article in which it has identified TTPs, it can map the content of that article to the ATT&CK navigator so that cybersecurity teams can easily analyze the adversary behavior and compare it with their existing defenses.
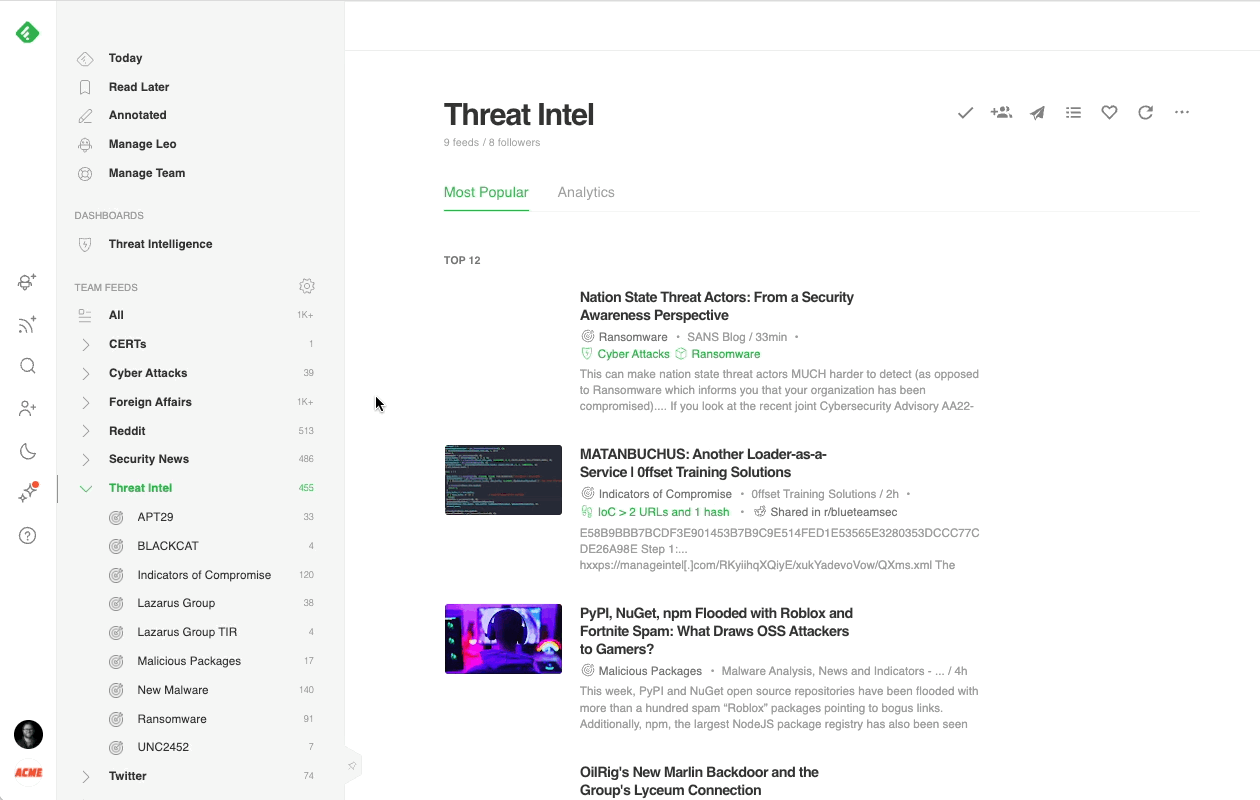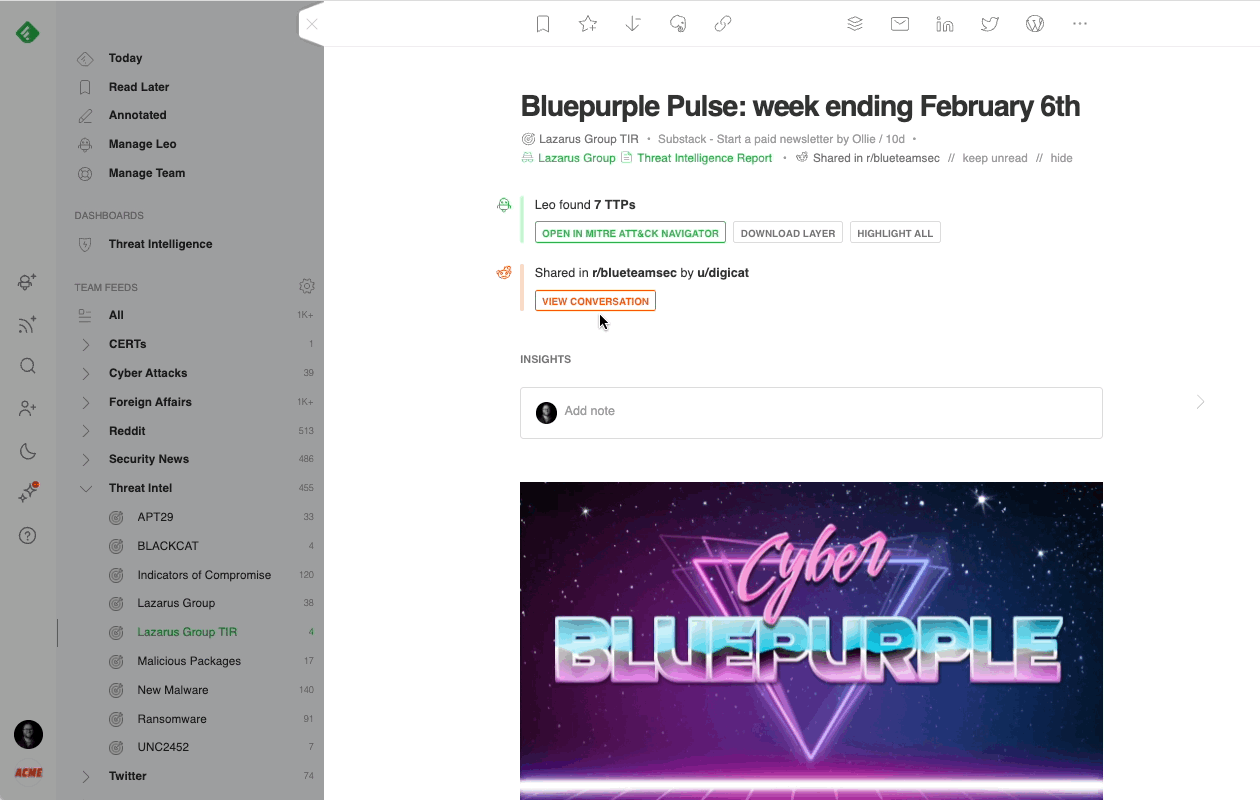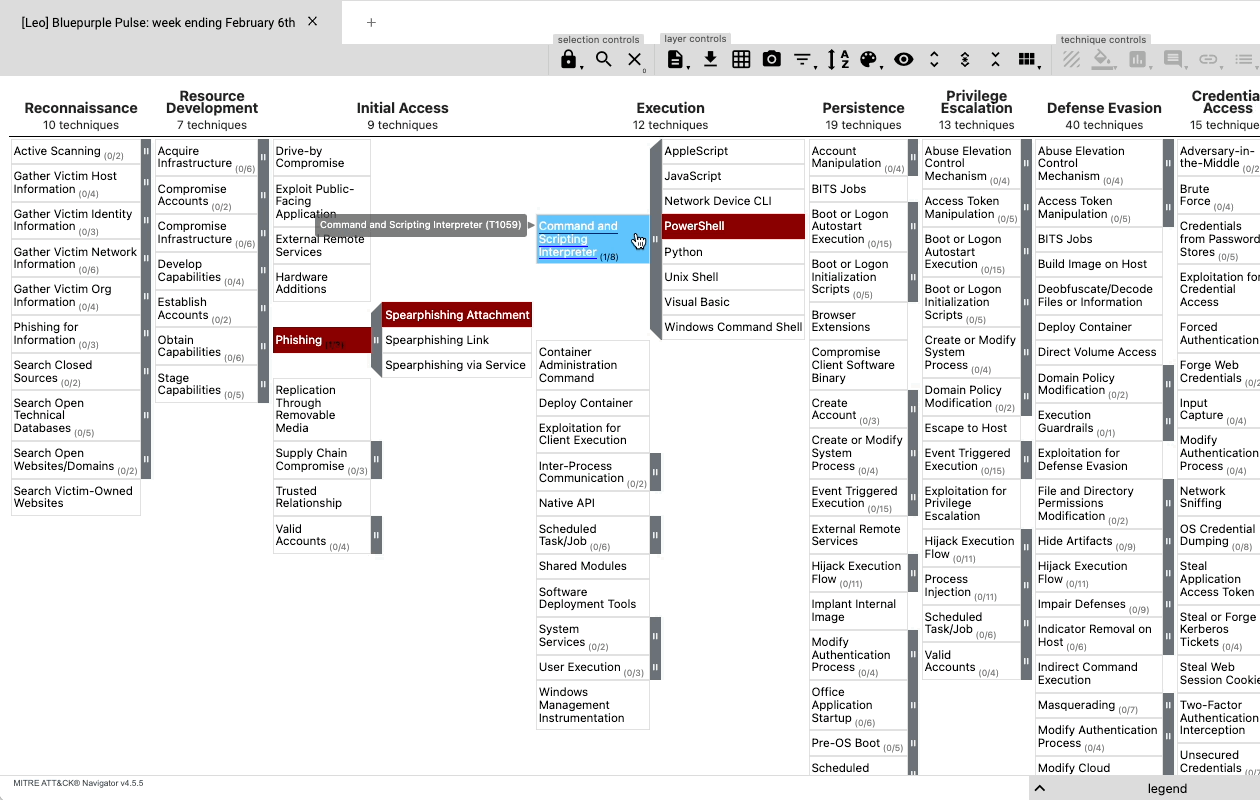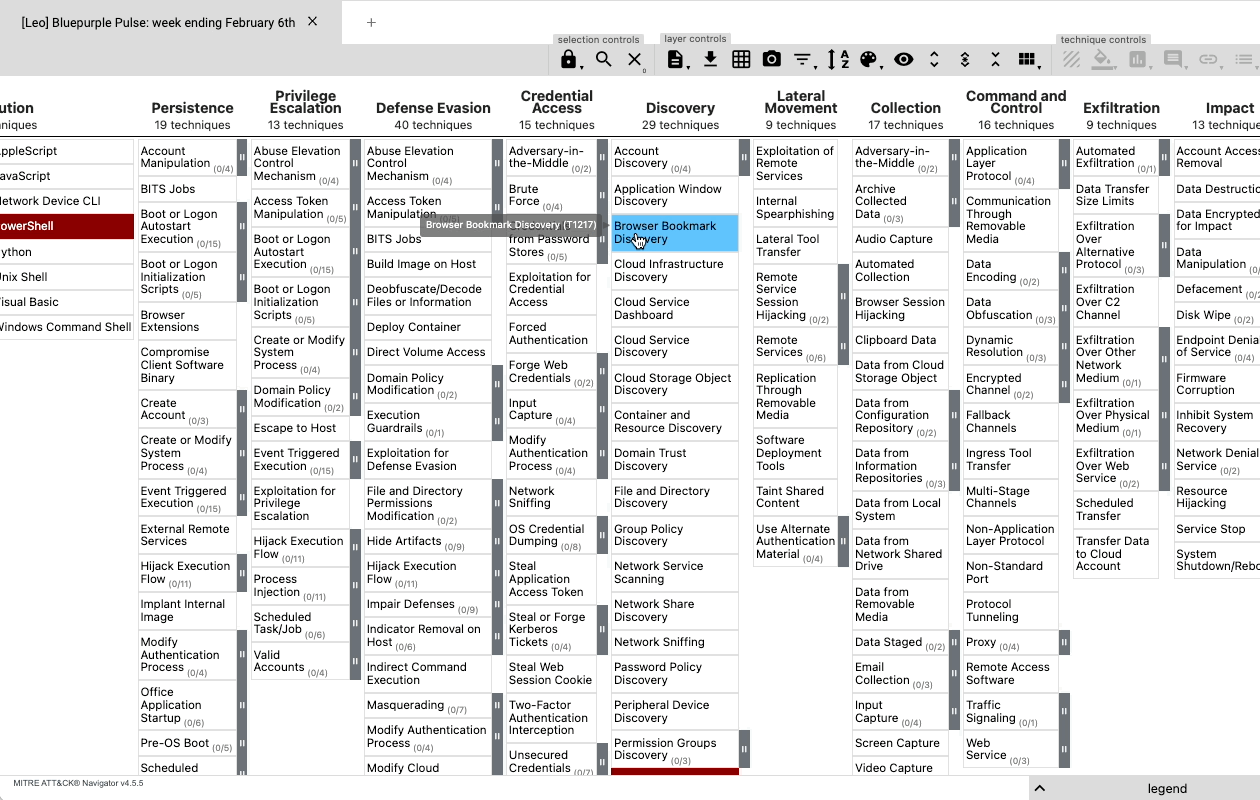
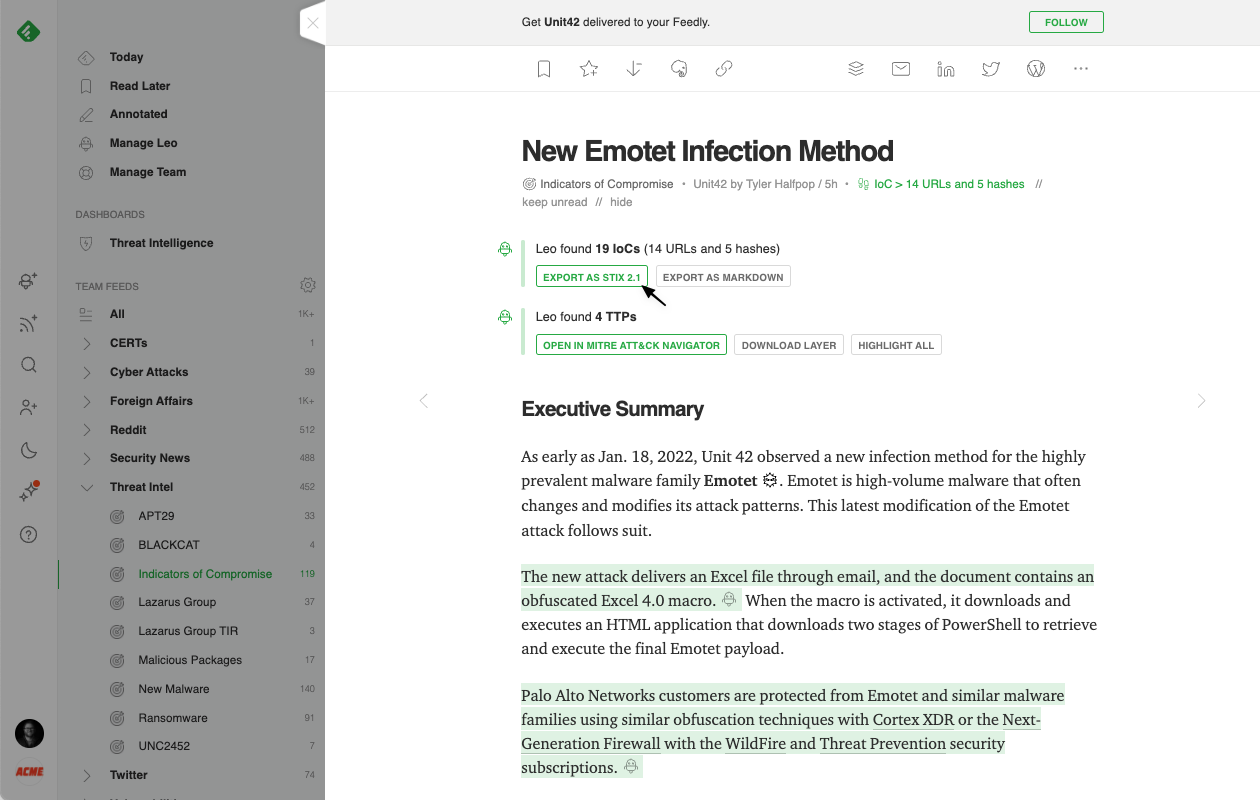
Feedly AI also automatically flags all the malicious IPs, hashes, domains, and URLs (IoCs) it identifies in articles so that they can easily be exported with links to threat actors, malware families, and vulnerabilities using STIX 2.1 and imported into Threat Intelligence Platforms (TIP).
Security teams can efficiently track cyber attacks targeting their industry or supply chain. Feedly AI has been pre-trained to understand the concept of a cyber attack and who the target of the attack is. Here is an example of how a cybersecurity professional might ask Feedly AI to track all the cyber attacks targeted at the finance industry.
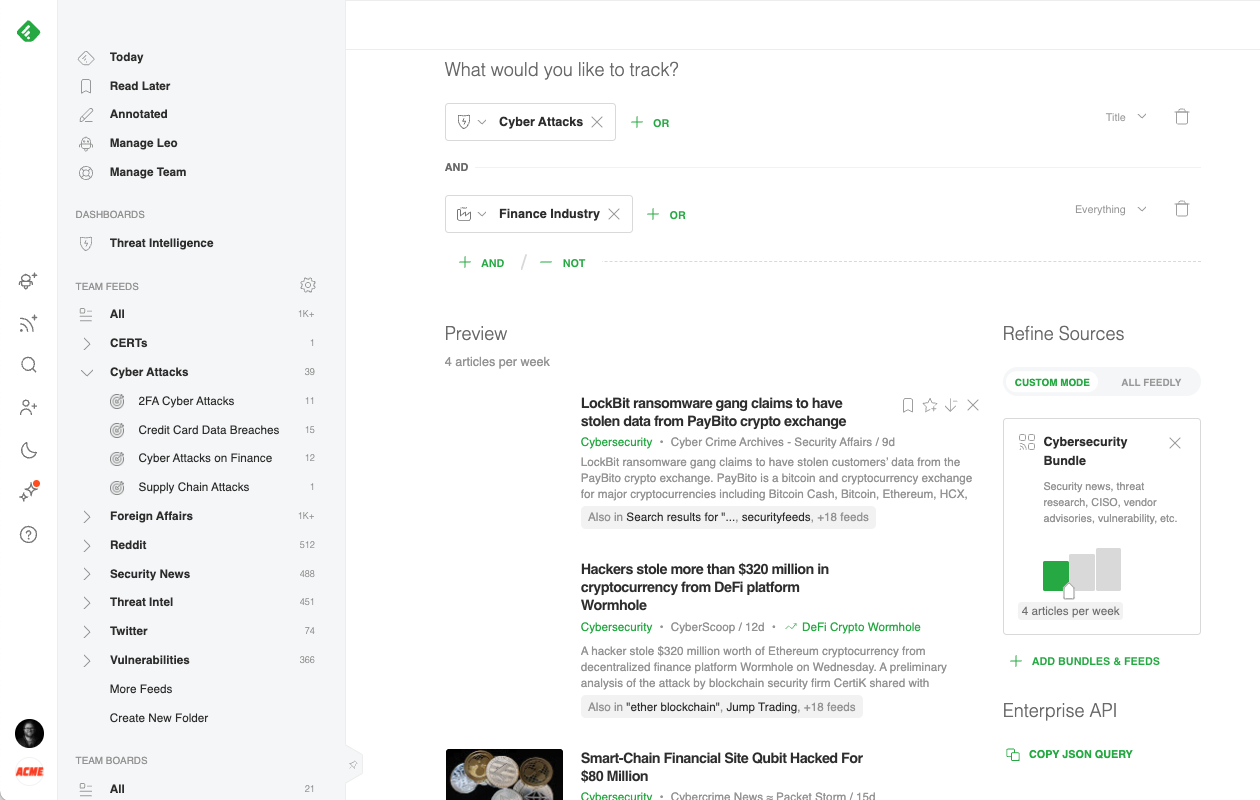
The focus can also be narrowed down to more specific threats like “data breaches impacting credit cards” or “cyber attacks using multi-factor authentication”
Feedly allows cybersecurity teams to follow a wide variety of trusted feeds all in one place, including websites and blogs, newsletters, Reddit communities, and Twitter accounts, searches, and hashtags. The teams that get the most out of Feedly turn it into their one-stop intelligence center so they can share common sources in one place. They end up saving hours each week because they’re no longer sharing articles ad-hoc across email, Slack, and other messaging platforms.
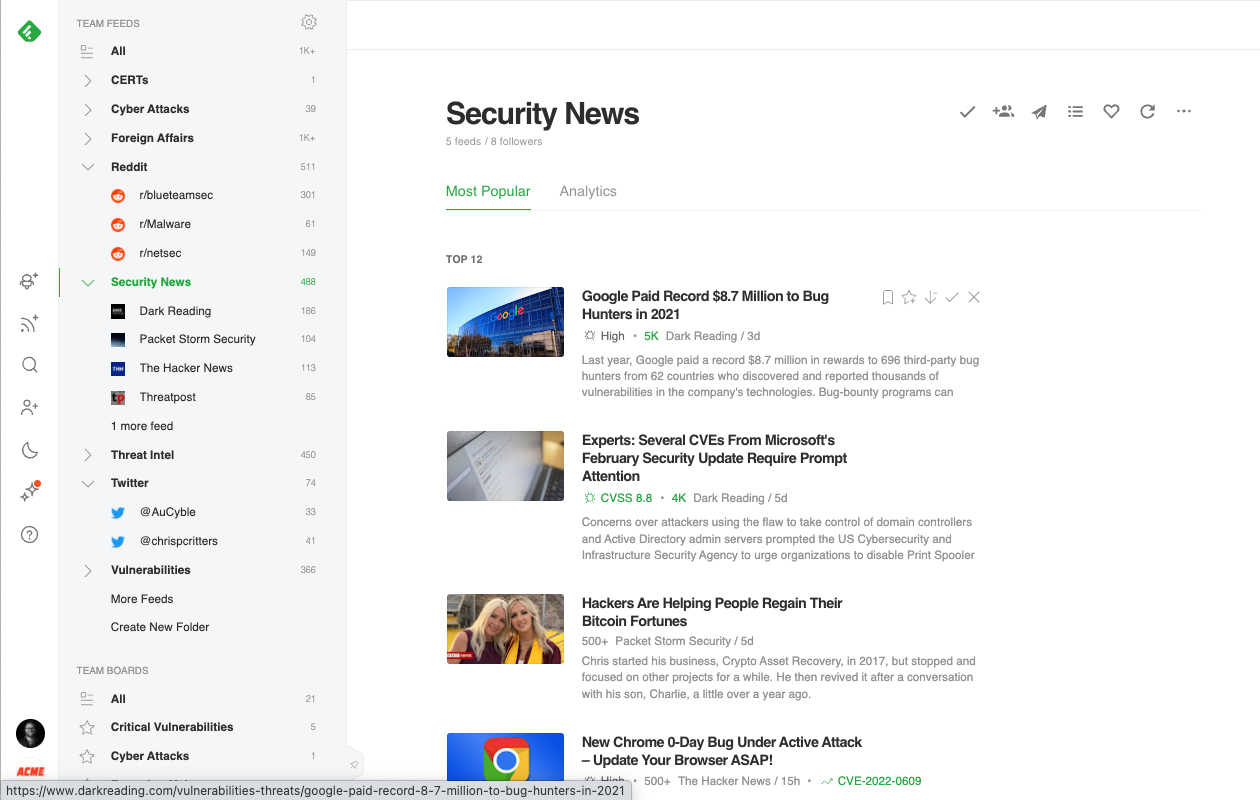
When an article of importance surfaces, Feedly provides the tools to annotate, highlight, add notes, and save the article to a Board for review later. When an article is saved to a Team Board, Feedly for Threat Intelligence users have additional options to auto-generate Newsletters, share with Slack or Microsoft Teams, or use Feedly’s Rest API to integrate into an existing workflow.
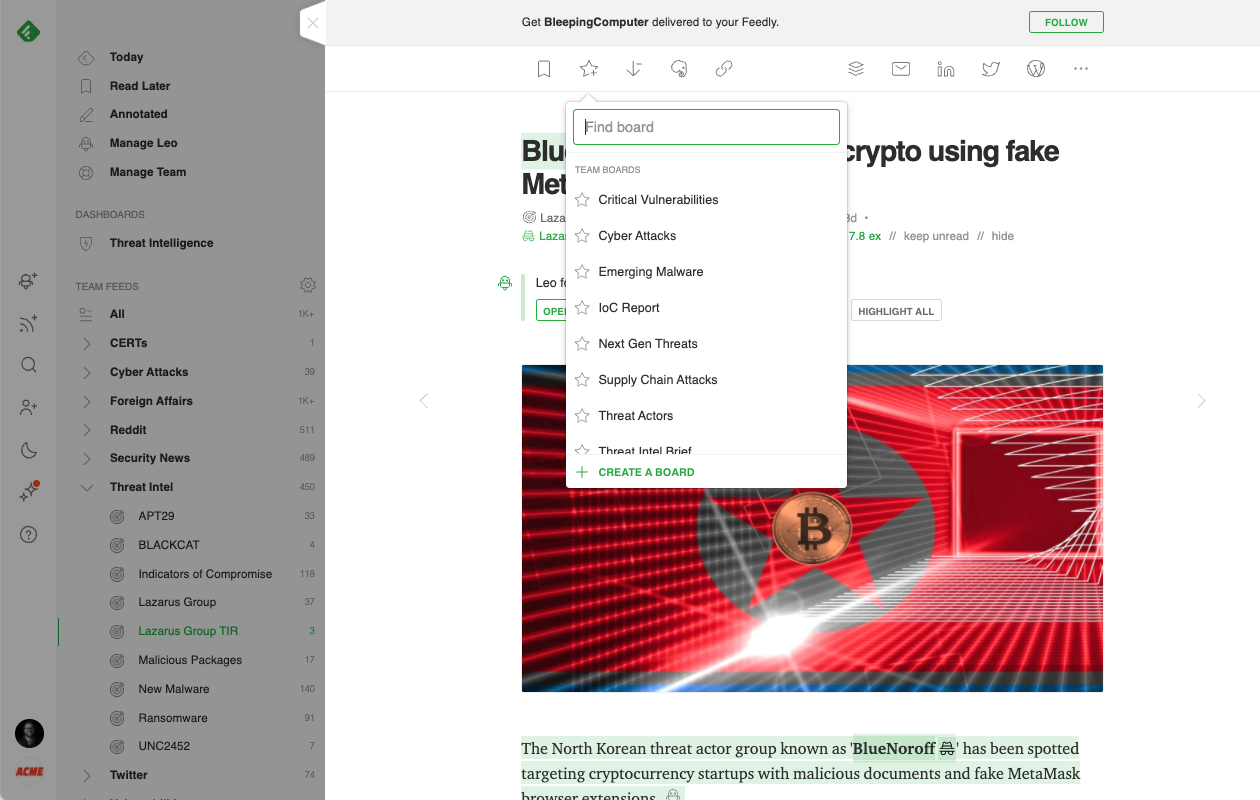
Here are a few examples of Team Boards that have helped cybersecurity teams stay organized:
All of these features, plus many more, are available as a part of Feedly for Threat Intelligence. To learn more about any of these features, or start a free 30-day trial, click the link below.

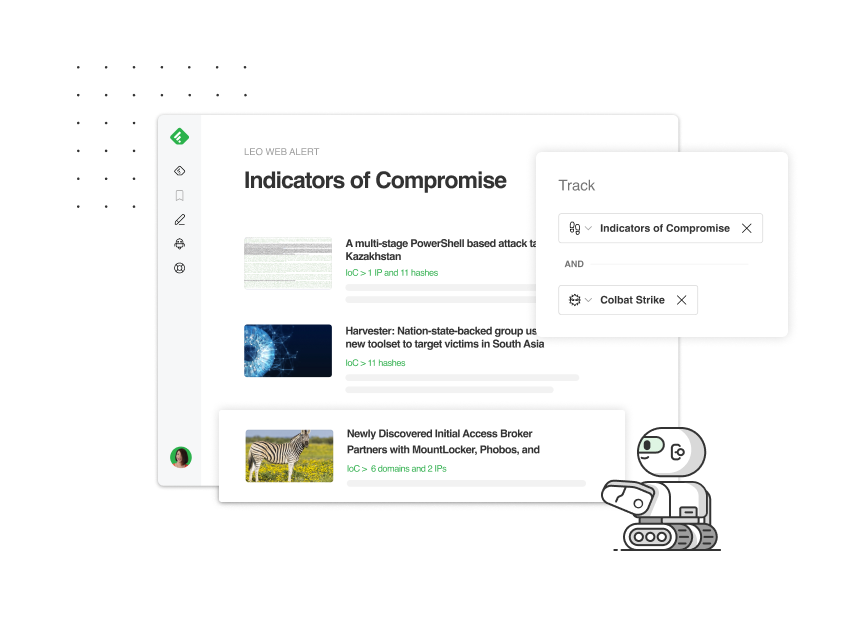
Leo recognizes IoCs mentioned in articles, and can gather them for yo

An inside look at how the Airbus CyberSecurity team is using Feedly to monitor and share actionable insight

Finding and collecting relevant indicators of compromise is critical to your security, but with millions of articles to sort through, discovering and collecting the right ones is a challenge. Even if you know where to look, IoCs can be easy to miss and tedious to upload to your threat intelligence platform.
This is why we’re excited to announce that now you can discover, collect, and export malicious IPs, domains, hashes, and URLs mentioned in your Feeds or across the web, because Feedly AI recognizes indicators of compromise.
We trained Feedly AI to understand, find, and even export IoCs, so that they are easier to find and prioritize. This feature is included with Feedly for Cybersecurity.
“Being able to track IoCs with Feedly has been very helpful, our team has been using the new feature every day to be on top of potential risks. Just today, Feedly AI was able to spot three IoCs in a long report I was reading although I hadn’t noticed them.”

Michelle Barro, Threat Intelligence Analyst at Verizon
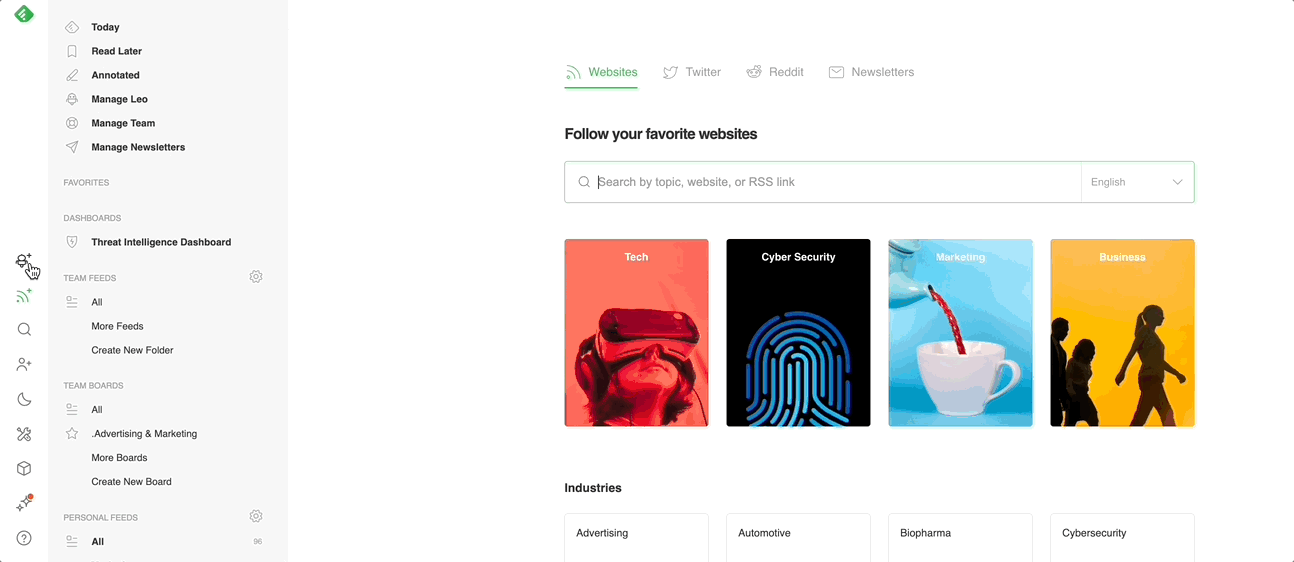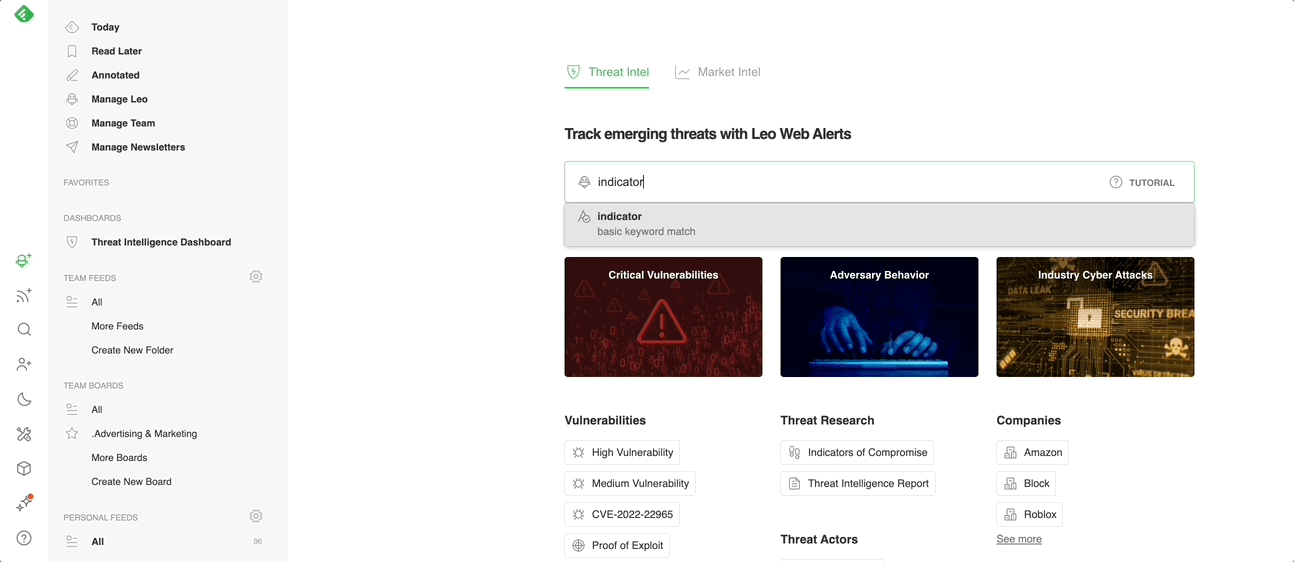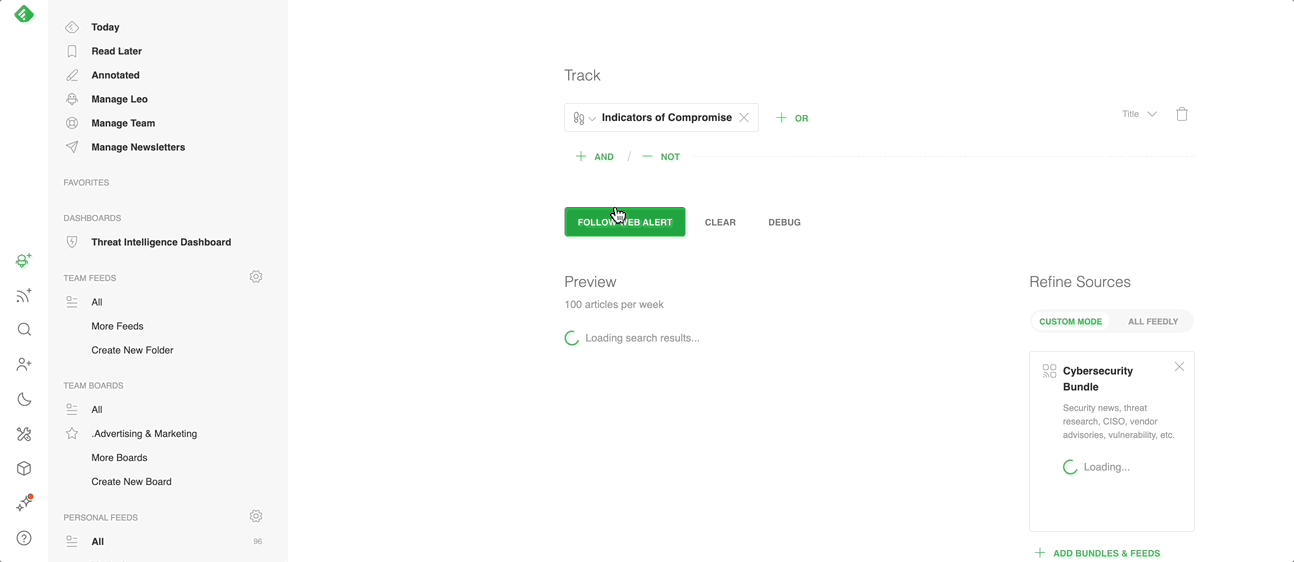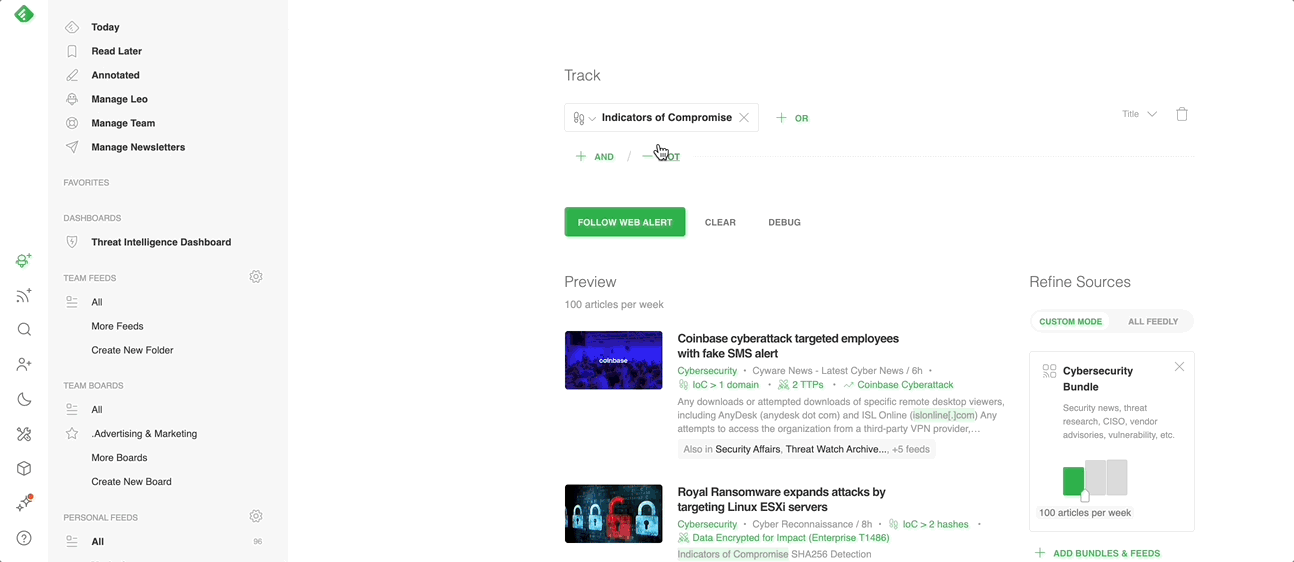
Feedly AI recognizes malicious IPs, domains, hashes, and URLs within the text of articles, Tweets, or Reddit posts, and tags articles so you know how many and what type of IoCs appear in a given article.
When an article contains an IoC, Feedly AI will highlight it for you so it’s easy for you to find and confirm, even if it is buried in the text of a long article or threat intelligence report.
If the IoCs are relevant, you can export them to a markdown or STIX file that will include critical context such as the article link, malware, threat actor, CVE, product, and TTP information.
To track indicators of compromise from across the entire web, click the robot symbol on the left hand navigation menu, and navigate to the ‘Threat Intel” tab. Type “Indicators of Compromise,” then click “+ AND” to refine your AI Feed further if needed.
Now that I can use Feedly to track IoCs across the web, our process to upload new indicators to our environment is much faster and easier. Being able to track IoCs across millions of sources on the web helps us cover every base possible.”
Cybersecurity engineer at a leading Fortune 500 technology company
Feedly for Cybersecurity is an OSINT platform used by more than 100 cybersecurity teams globally to speed up their threat intelligence. See how Feedly can help you conduct threat research up to 70% faster by starting a free trial.
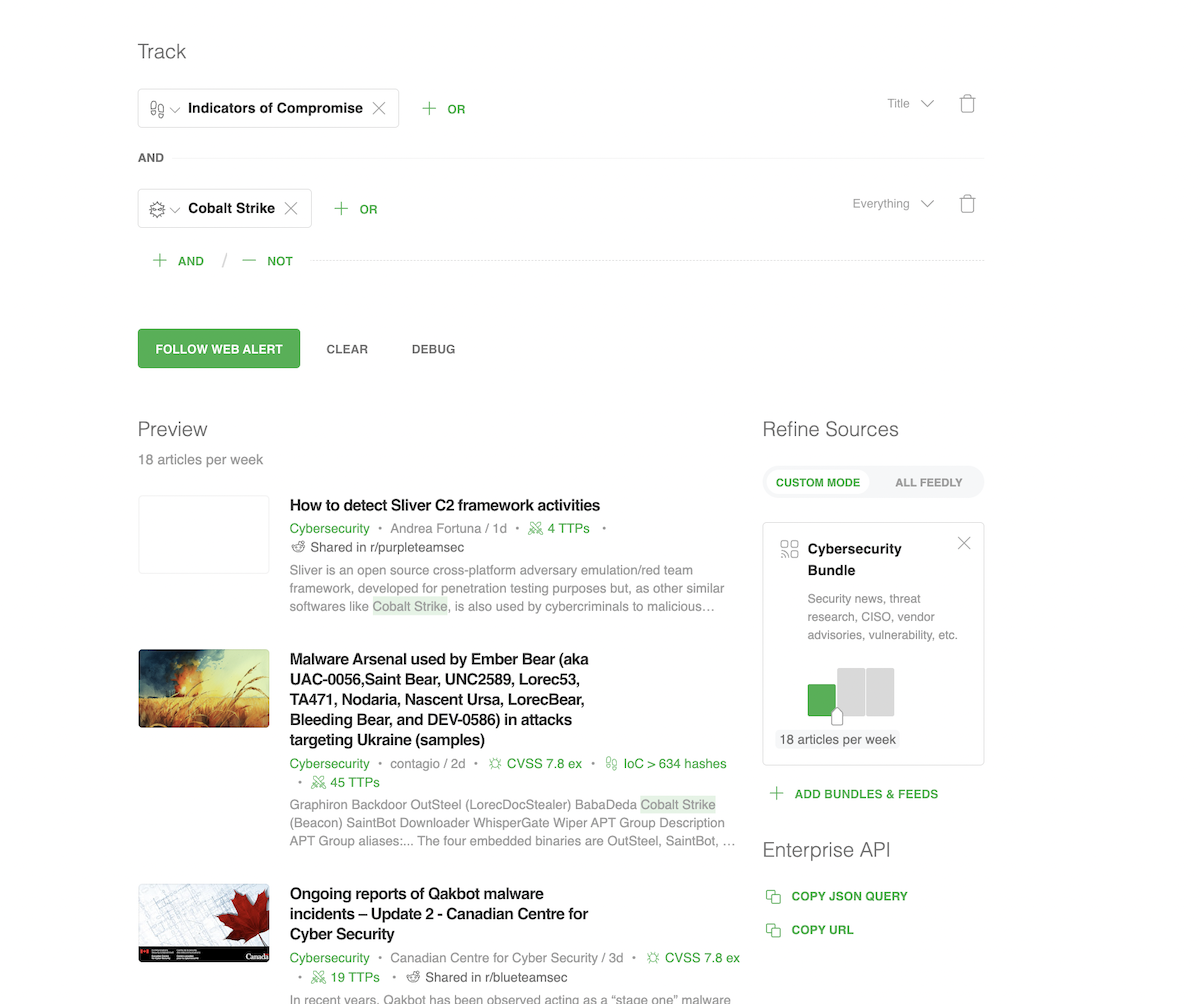
Let’s say you want to search for indicators of compromise related to a specific threat actor or malware. You can use AI Feeds to flag IoCs that match your query, even if the articles are from sources you don’t specifically follow.
The AI Feed shown in the example below will look for IoCs related to the Cobalt Strike malware family, making it easy to find what’s relevant, export it in seconds, and proactively monitor the web for future IoCs relevant to you.
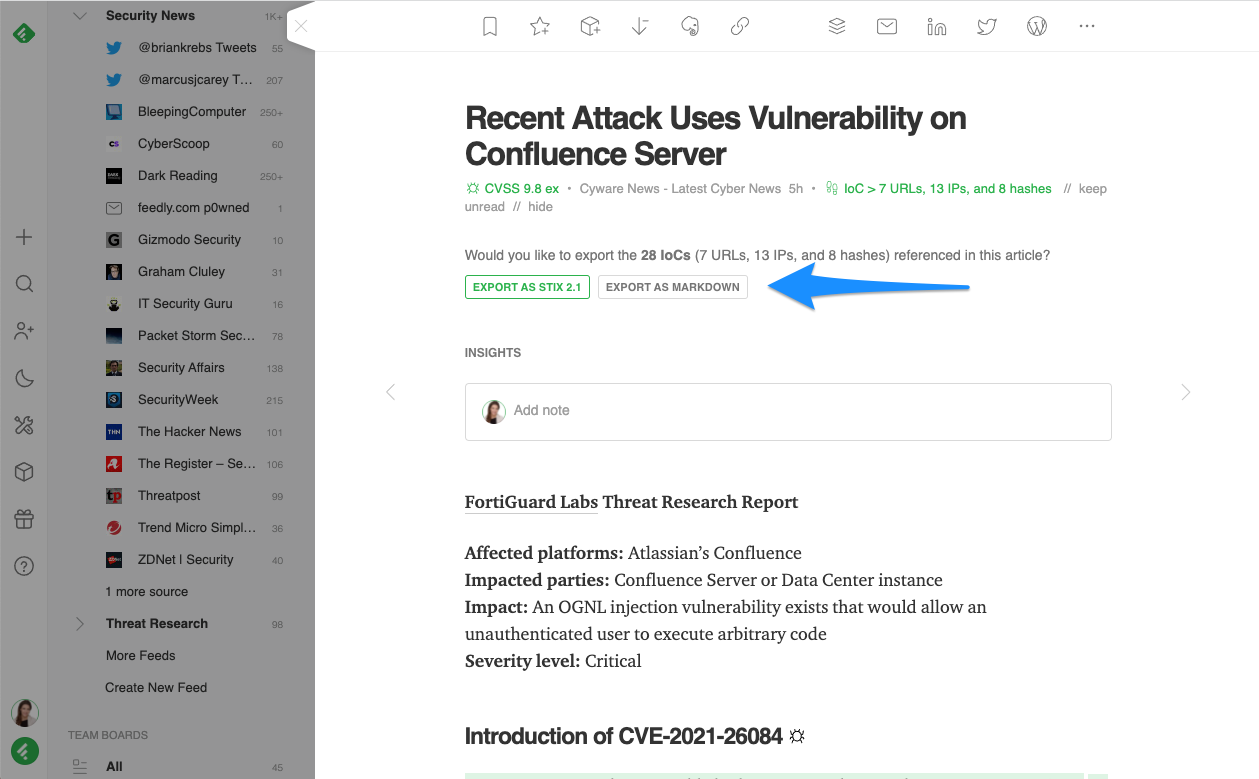
When you open article(s) that contain IoCs you’d like to upload to your preferred threat intelligence platform, you can export them in either STIX or Markdown formats. This is a significant time saver in contrast to scrolling through the article and copying and pasting what you need.
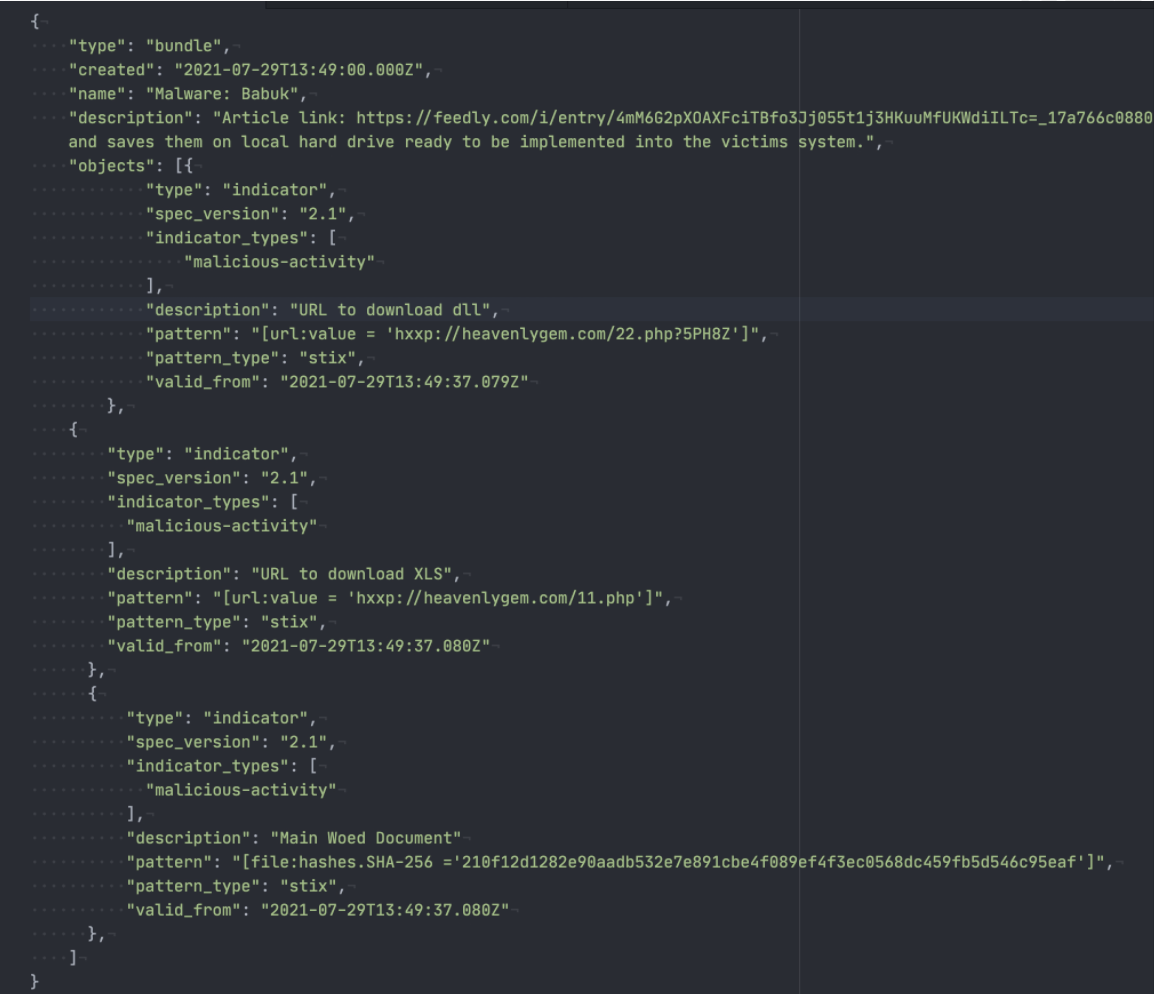
Your export will also include the IoC context such as the original article link, related malware, threat actor, CVE, product, and TTP information. This makes it even easier to take action. Here is an example of a STIX export:
The Advanced Feedly for Cybersecurity plan includes up to 100,000 requests per month and the full power of the Feedly API. Any action a user is taking in the Feedly application can be performed via the Feedly API, including collecting IoCs. You can access instructions for doing so here.
You can use the Feedly API to aggregate indicators of compromise and their context (associated threat actors, malwares, vulnerabilities and TTPs) from recent articles in a Feed, and return a single STIX object with all of those components and their relationships.
To learn more about the power of the Feedly API or begin a trial or proof of context, click here.
It used to be particularly tedious to track the IoCs that are related to the critical UI CVEs or products my team has to be on top of. Now, with Feedly’s new IoC feature, I can track IoCs in a much faster and more visible way.”
Michael Rossi, Independent Security Consultant
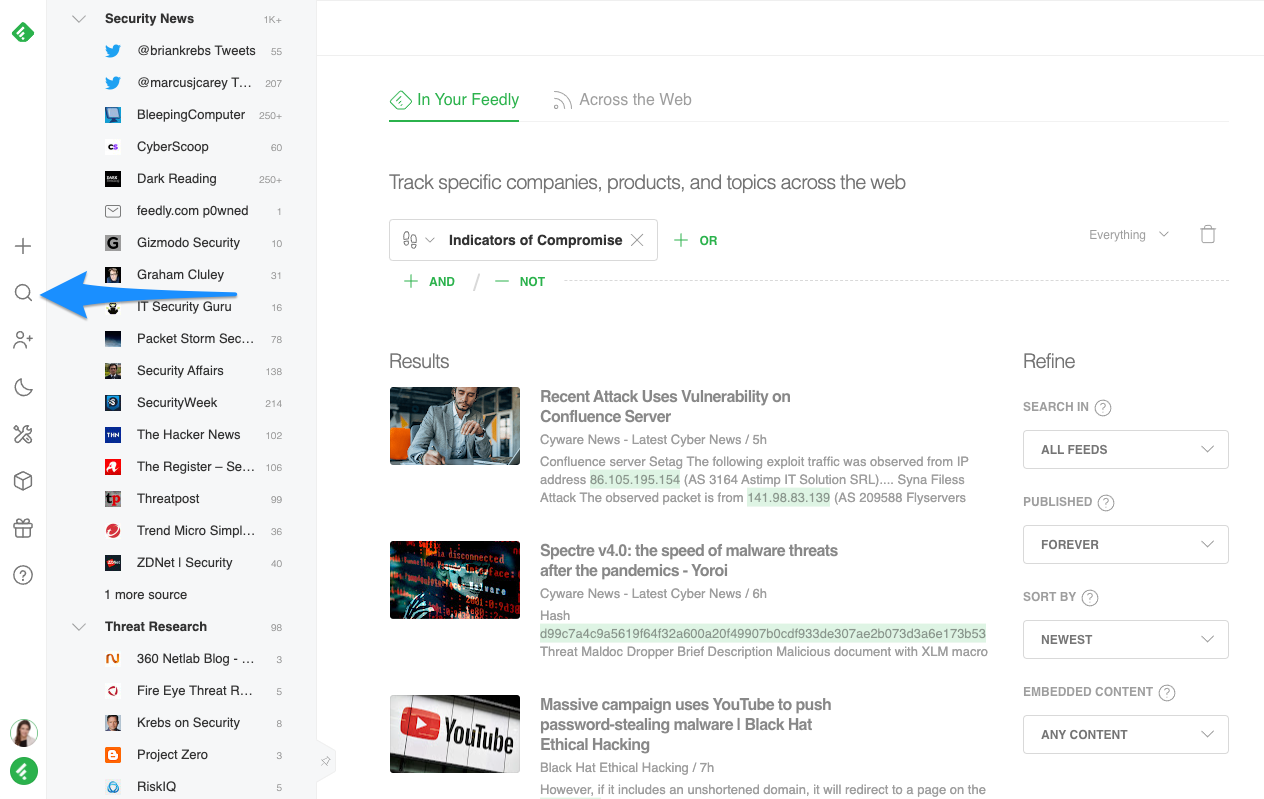
Finally, if you need to search for a specific set of IoCs already published online, you can do this via Power Search. Power Search allows you to leverage Feedly AI’s knowledge graph within your existing Feeds or across the web, allowing you to get much more granular and accurate than standard web searches.
Click the “ ” icon in the left navigation menu to access the Power Search screen. From here, you can look for any articles that contain indicators of compromise. This is ideal when you need to track a malware family you haven’t tracked before, and want to quickly find known IoCs that are already available online.
” icon in the left navigation menu to access the Power Search screen. From here, you can look for any articles that contain indicators of compromise. This is ideal when you need to track a malware family you haven’t tracked before, and want to quickly find known IoCs that are already available online.
The Indicators of Compromise feature, CVE dashboard, cyber attacks Smart Topic, and several more advanced features are included with Feedly for Cybersecurity. This enterprise package is perfect for cybersecurity teams that need to conduct open-source threat intelligence more efficiently. To learn more about any of these features, or start a free 30-day trial, click the link below.
Feedly for Cybersecurity is an OSINT platform used by more than 100 cybersecurity teams globally to speed up their threat intelligence. See how Feedly can help you conduct threat research up to 70% faster by starting a free trial.


This analyst team designed AI-powered security Feeds in Feedly that proactively alert them about specific topics, threats, and threat actor
Drew Gallis, analyst at WillowTree, leverages Feedly for Cybersecurity to track cyber threats across the company’s supply chain and protect client
The only constant in the realm of cyber security is change; hackers are continuously maturing and becoming more sophisticated, attack patterns are constantly evolving, and the threat landscape is growing more volatile every day; one cyber attack occurs every 39 seconds.
That’s why we’ve enhanced Feedly AI’s knowledge of cyber attacks, targets, and industries so you can keep pace with the threat landscape and do what you do best: maintain the integrity of your security posture. You can ask Feedly AI to flag critical cyber attacks in your feeds and focus on specific attacks targeting your industry or supply chain. You can also push attack insights to your internal platforms via the Feedly API.
Feedly AI flags important information to focus your efforts on targeted insights. Feedly AI understands cyber attacks because we taught him about malware, ransomware, data breaches, phishing, social engineering, and fraud.
You can train Feedly AI further and have him focus on the specific topics, threats, and threat actors you care about to gain a deeper understanding of the threat landscape as it applies to you.
From a proactive monitoring perspective, the power of using Feedly AI is to actually inform you of breaches before anyone else knows.”
Cybersecurity Analyst at a top energy provider
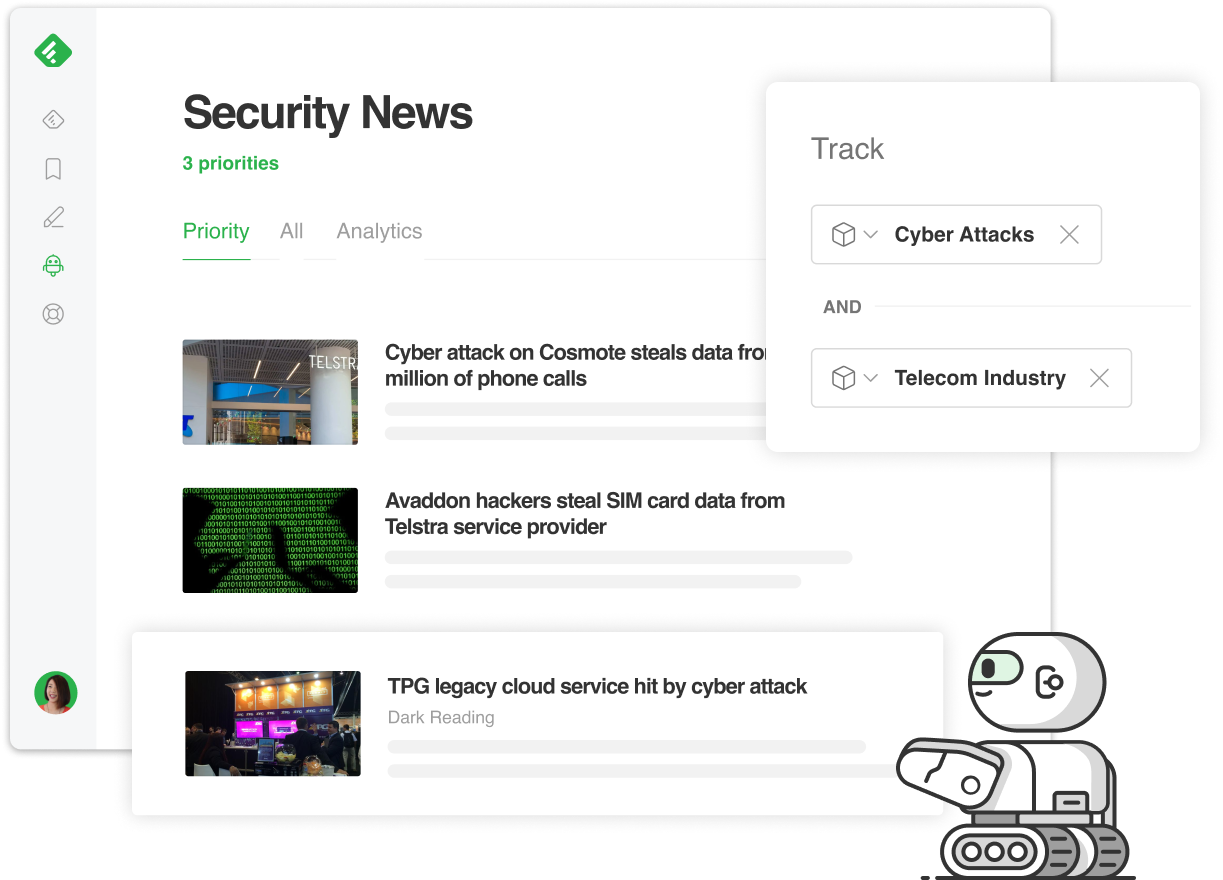
You can start by training Feedly AI to recognize cyber attacks as a smart topic, a concept that Feedly AI has been trained to understand with our AI models. Simply navigate to the security category you want to add this insight to and enter “cyber attack” as a topic. Training Feedly AI to highlight cyber attacks in your security feed keeps you up-to-date with the most recent reports. Highlighting the attacks that are actually being conducted in the wild helps you effectively prioritize and ensures you never miss a thing.
We’ve taught Feedly AI to recognize 19 industry sectors to ensure you always have the most current industry-relevant threat intelligence at your fingertips. Don’t see your industry? No problem! Ask us and we’ll teach Feedly AI to recognize it.

We were able to turn the list of our top partners into an AI Feed and ask Feedly AI to flag cyberattacks targeting those partners. That’s how we identified that one of our vendors had been breached a week before that the actual company told us.”
Cybersecurity Analyst at top energy provider
Feedly AI also recognizes each company listed in the Forbes Fortune 500 list to help you optimize and maintain your vendor security initiatives.You can gain these deeper insights simply by adding the industry or company you want Feedly AI to flag for you.
You can use Feedly AI to detect new risks, reinforce your vendor risk programs, and potentially be the first to discover a breach.
Track up to 1,000 vendors in your supply chain to see the most relevant cyber attacks early.
Supply chain attacks have been in the limelight recently. Now, Feedly AI can help you cross-reference your known vulnerabilities with the latest threat intelligence. Proactive alerting informs you of critical vulnerabilities, cyber attacks, and emerging threats before anyone else. Need to know about zero-day exploits as soon as they are targeted? No problem. Need to create your own list of companies you want to track? Feedly AI has your back.
Every second counts in cybersecurity. You tell Feedly AI what you want and it populates the insights you need, when you need them.
Feedly AI does the work upfront so you can filter out the noise and save massive time, working smarter and faster. Up to 80% faster.
Before using Feedly AI to track cyber attacks, we would struggle with an overload of data and waste time sifting through information. Our feed is now 2-3 times shorter, we do not miss out on any important cyber attacks and we earned back so much time!“
Anonymous Cybersecurity Analyst
The Cyber Attack AI Model is one of the advanced AI skills in the Feedly for Cybersecurity package.
Contextualized CVE information for faster threat research, without the overwhel

This analyst team designed AI-powered security Feeds in Feedly that proactively alert them about specific topics, threats, and threat actor
Cyber attacks are increasing in volume and sophistication across every industry and category, leaving threat analysts and frontline security teams faced with a flood of information. The consequences of missing critical information are astronomical, but no human can keep up with this onslaught of data on their own.
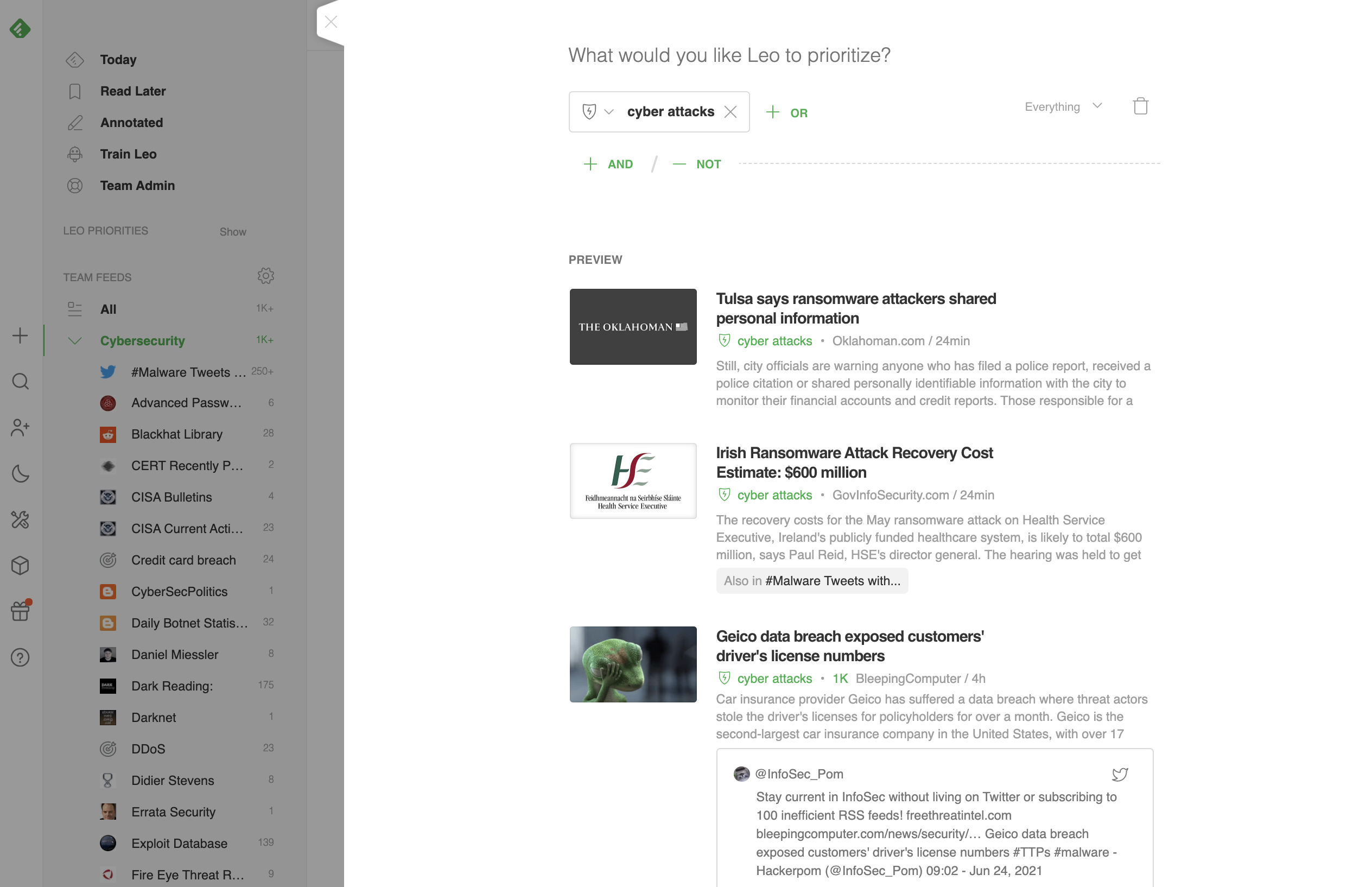
You need relevant, real-time, accurate information – and scrolling through an endless list of sources won’t get you there. That’s why we’re excited to announce that Leo, your AI research assistant, now aggregates information on vulnerabilities, exploits, malware families, and threat actors into a single view so that he can help you proactively track and research CVEs.
Leo CVE Intelligence Cards gives you at-a-glance visibility into relevant trending vulnerabilities, and you can use Leo to focus any of your feeds for faster insight into risks impacting your business’s software, hardware, and application stack.
Information overload is real. This is why we enhanced Leo’s cybersecurity knowledge graph so he can help you proactively track and research critical vulnerabilities and zero-day exploits relevant to you.
With Leo, you can prioritize the CVEs that impact your organization’s technology stack and reduce the time it takes to investigate threats by up to 70%. All of this information is available at a glance via Leo CVE Intelligence Cards and throughout your Feeds.
Before using Feedly for Cybersecurity, my biggest challenge was to quickly sort through all the data to find the top CVEs by mention, and track their relationships with exploits, patches, etc. It would take a lot of work to search through unstructured text and large bulk files. With Leo, it’s so much easier to quickly review details of a CVE and its associated relationships.”
Michael Rossi, Independent Security Consultant, Cybeta
If you want to dive deeper into a CVE, exploit, or threat, Leo synthesizes vulnerability, patch, exploit/PoC, malware, and threat actor information into a single CVE Card. Leo eliminates the time you used to spend opening a new browser tab, searching, browsing for the resource you want, and skimming everything individually to find what mattered.
Instead of having dozens of research tabs open in your browser, Leo CVE Intelligence Cards consolidate the information into a single location where you have at-a-glance views of:
For new vulnerabilities that don’t have a CVSS assigned yet, Leo uses a proprietary NLP model based on the CVSS v3 methodology to forecast this score. This way, you can spot new threats and take proactive steps in real-time.
Color-coding helps you make quick decisions about the next steps in your investigation. The darker the color on the Awareness graph, the more people are talking about the CVE across the web.
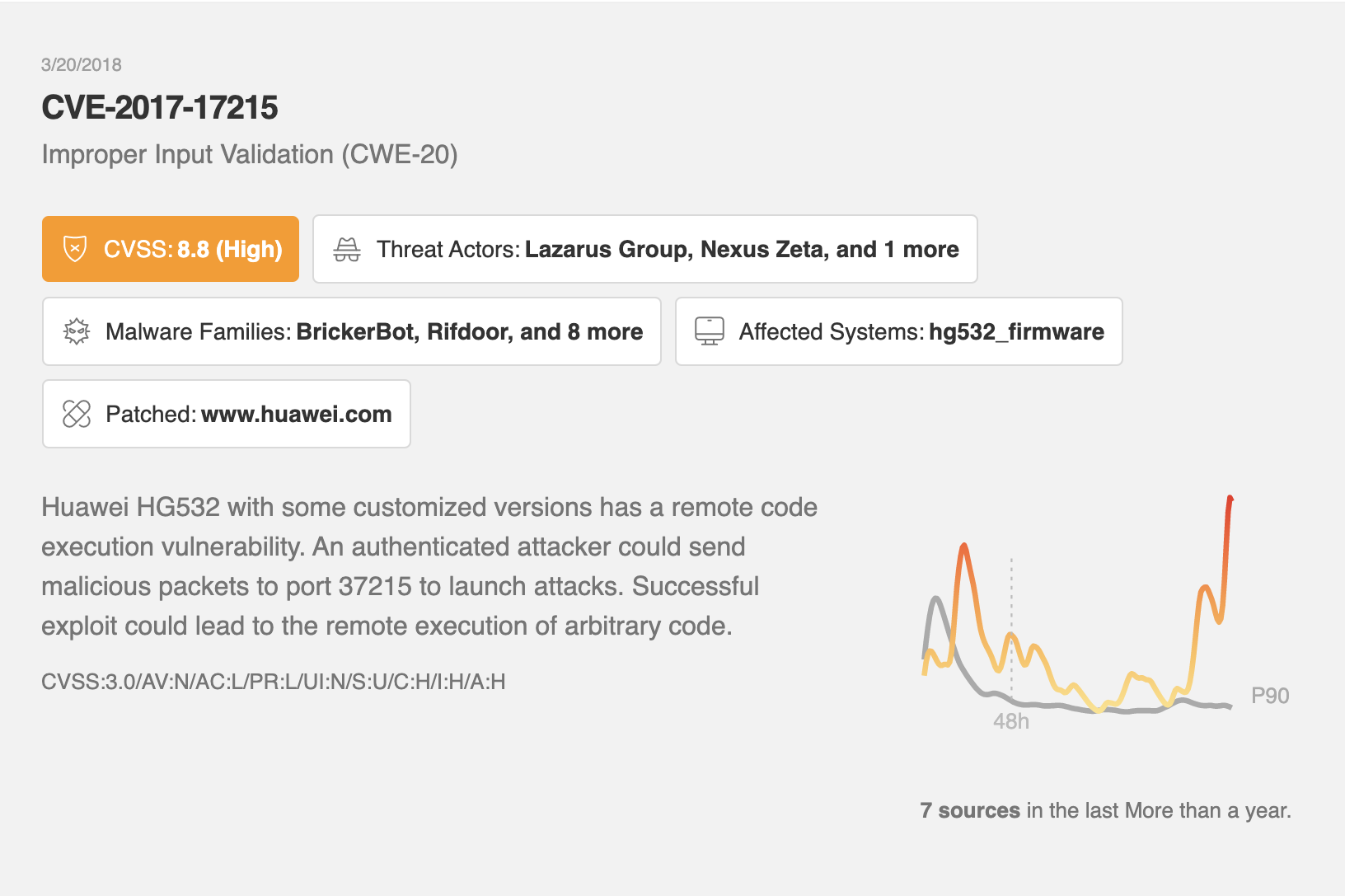
Leo provides links to all the external resources you need to investigate the CVE, so you can more rapidly respond to threats and improve important cybersecurity metrics like mean time to detection (MTTD), mean time to investigate (MTTI), and mean time to remediate (MTTR).
Dig deeper, faster, to determine if a specific vulnerability represents a critical risk for your organization based on its technology stack to decide whether to flag the intel and share it with the rest of your team.
For example, you can click on “Affected System” or “Patched” to go directly to those sources like the National Institute of Standards and Technology (NIST) National Vulnerability Database or websites with patches for remediation purposes.
“Before using Feedly for Cybersecurity, it was hard to prioritize which vulnerabilities were more important at a glance and determine if they applied to our networks. Now that we use Leo, we have been saving so much time, it’s much appreciated!“
– Feedly for Cybersecurity Customer
In addition to his interactive CVE Cards, Leo also prioritizes the most recent and talked about CVEs, right on your Today page. Simply click on a CVE name to see the dashboard complete with the information necessary for critical decision-making.
Leo knows cybersecurity because we taught him about CVE, CVSS, exploits, patches, threat actors, and other security intelligence concepts. Leo summarizes the information from various resources including NVD, vendor advisories, blogs, Twitter, and Reddit so you don’t have to check each location, sifting through posts unrelated to the CVE you care about.
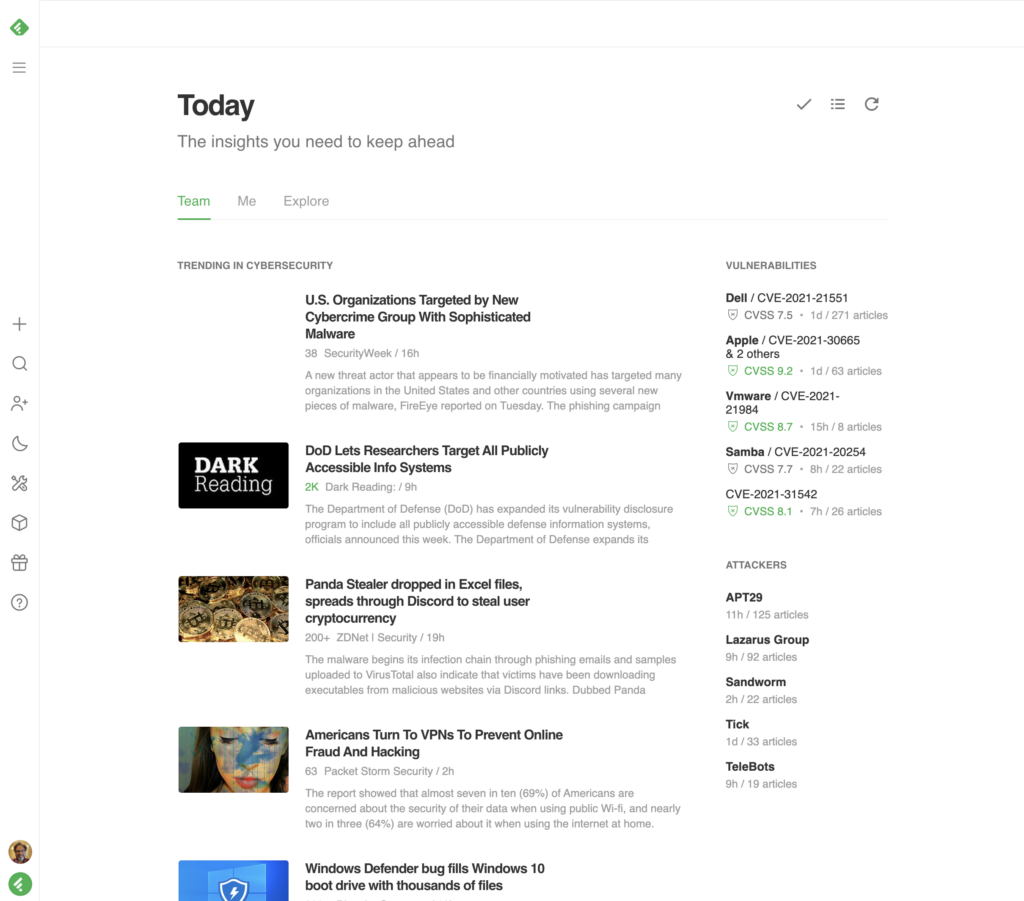
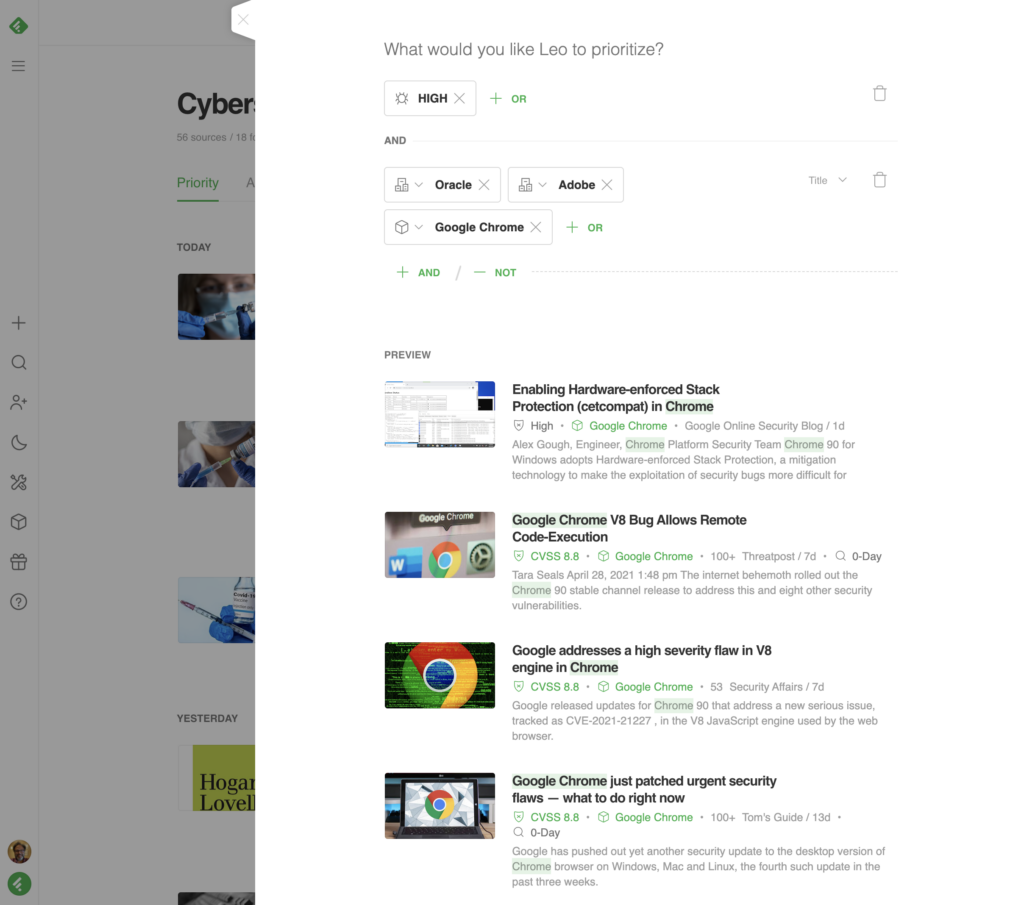
You can add new Leo Priorities on top of your current feed to add contextual business risk. For example, if your technology stack includes Oracle, Adobe, and Google Chrome, but not Samba, you can refine Leo’s priorities so you only see what’s relevant to your organization.
Train Leo to prioritize vulnerabilities based on CVSS score to increase the relevance of your feed. Leo can flag risks related to your organization’s unique technology stack so you can out pace attackers.
You can start by training Leo to surface CVE’s based on Qualitative Severity Rating Scale — choose our preset for “high” or specify the CVSS scores to build your organization’s context into what you see.
Training Leo by using “HIGH” in combination with either products or vulnerability types personalizes your feed based on your organization’s unique needs. This lets you focus on the risks specific to your organization, weeding out the information you don’t need.
All of these features, plus several more, are available as a part of Feedly for Cybersecurity. This package of Leo skills, enterprise features, and advanced knowledge graph access is perfect for cybersecurity teams that need to reduce noise and quickly identify risks. To learn more about any of these features, or start a free 30-day trial, click the link below.
Save time researching CVEs so you can spend more time securing them.